What is Shadowsocks?
Shadowsocks is a free tool for those who want to bypass blocks in a simple but unpopular way. It is a network protocol with data encryption. It also helps protect traffic and personal data. It is based on SOCKS5 technologies, and the source code is available on GitHub.
The project started in 2012. Chinese developer Clowwindy released the first developments of Shadowsocks on GitHub. The protocol helped bypass the restrictions of the "Great Firewall", the great Chinese firewall. The project became popular worldwide after it was removed from GitHub, which attracted the attention of the media. Journalists suggested a connection between the removal and the attack on GitHub, which occurred a few days later.
Clowwindy stopped development in 2015 at the request of the Chinese authorities. Since then, the Shadowsocks community has been developing the project.
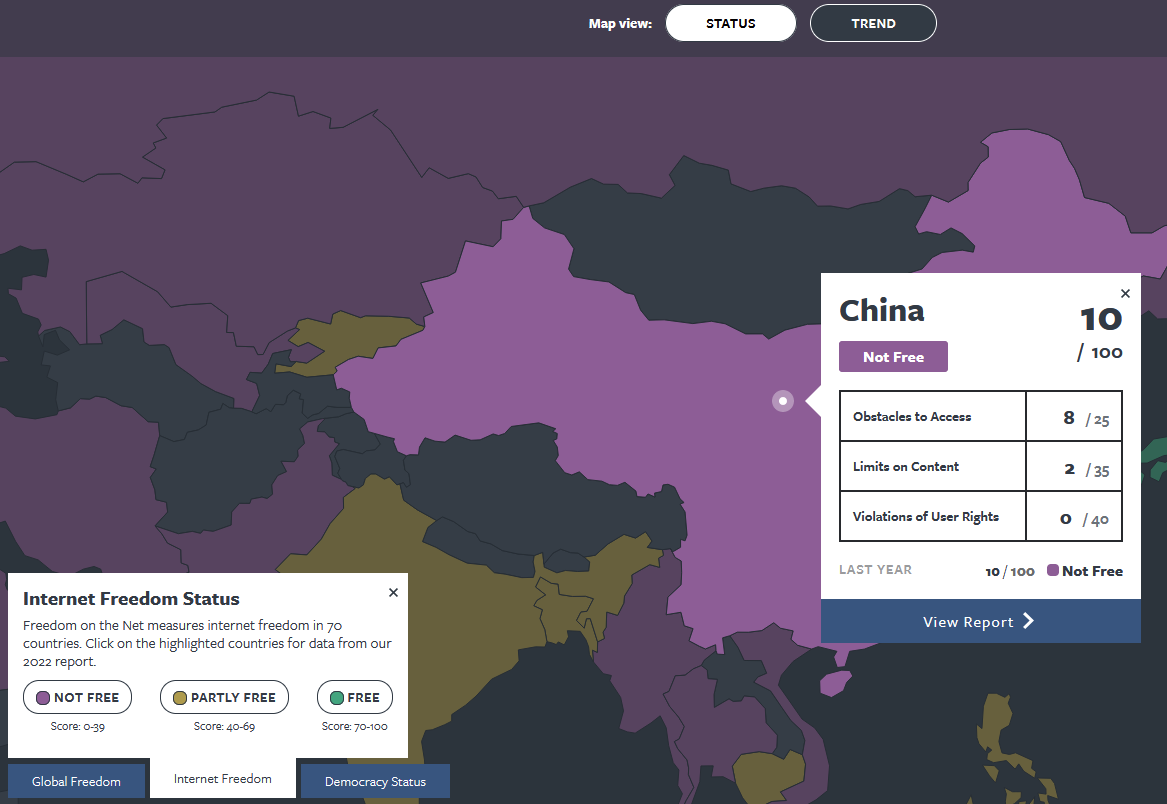
The map from the Freedom House website demonstrates in which countries Shadowsocks will definitely be useful.
Shadowsocks is needed for similar tasks to VPN:
- Bypassing blocks. Protocols are used to access blocked resources both in the country and by providers and operators.
- Protection of personal data. It is more difficult to access traffic and personal data.
- Secure connection from unprotected points - for example, through free Wi-Fi.
How shadowsocks works? Protocol explanation
With a standard network connection, the user connects to the internet directly through their provider. For example, if they want to visit a certain website, they first connect to the provider's router, and then to the website itself. If the state wants to block this website, they ask the provider to block access to its IP address.
To bypass this restriction, proxies are used. In this case, a "mediator" - a proxy server - is formed between the provider and the website. The connection still goes through the provider, but it only knows that the request is going to the proxy. Therefore, the connection to the website is unrestricted, and the traffic goes back to the user's device. But there are several problems here, for example:
- Sites and providers can detect that you are using bypass tools.
- The connection is not secure. However, you can use a proxy with encryption or a VPN, which most often encrypts traffic.
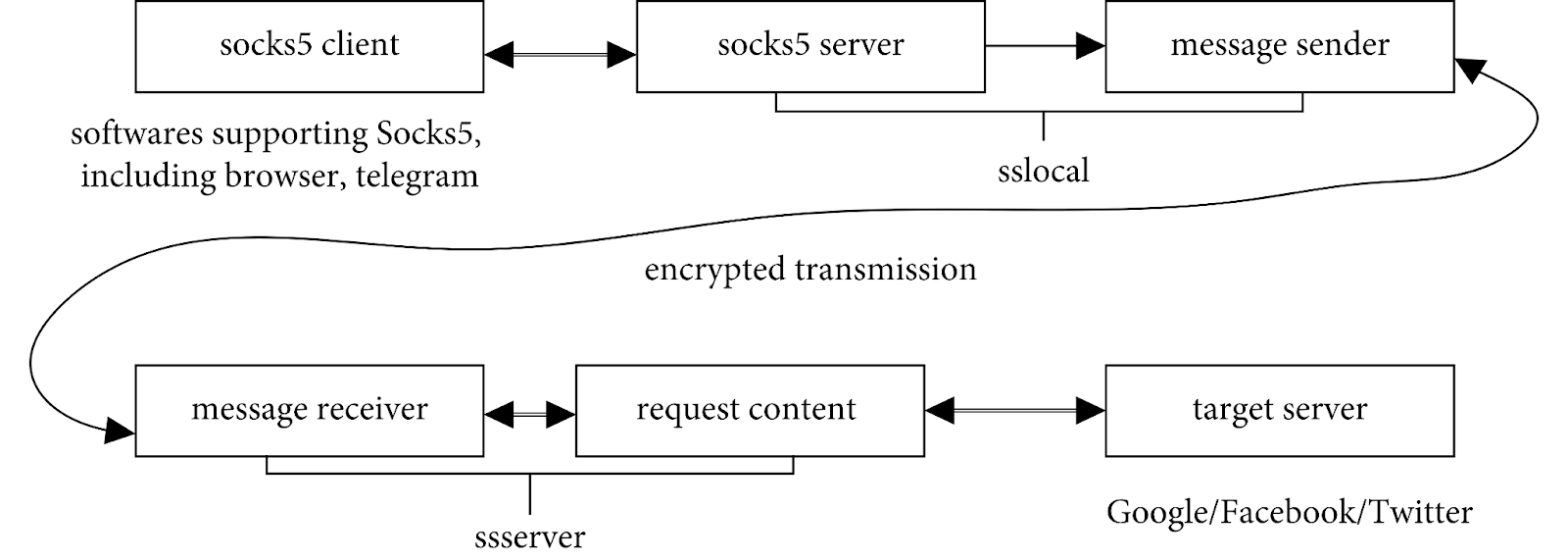
Shadowsocks is needed to solve these problems. Shadowsocks encrypts TCP/UDP payloads over a SOCKS5-like tunnel. To truly mimic HTTPS or HTTP headers, an additional obfuscation plugin (e.g., simple-obfs, cloak) is required. It encrypts data and presents it as regular HTML traffic. The protocol is based on SOCKS5, which has an article in our blog. It helps protect the connection through the AEAD algorithm.
AEAD uses the same principle as SSH tunneling, but in the case of AEAD, encrypted data also includes information about the source and recipient. This complicates the life of hackers. Even if they intercept a message, they cannot tamper with the data transmission.
Is Shadowsocks safe?
Shadowsocks is safe for basic censorship-bypass and typically faster/lightweight compared to a VPN. But, it’s not a substitute for a fully audited VPN when you need guaranteed anonymity, anti-DPI resistance, or enterprise-grade security. Shadowsocks is generally considered safe for censorship circumvention, but it has important limitations when it comes to strong security and detection resistance.
In general, AEAD (“Authenticated Encryption with Associated Data”) modes such as AES-GCM and ChaCha20-Poly1305 are industry standards and are generally regarded as very secure. There is no broad consensus that AEAD itself is “not so secure.” But according by discussions on Stack Exchange AEAD ciphers are considered not so secure. Anyway they are sufficient for a reliable connection and data protection.
Shadowsocks encryption method
Shadowsocks uses Authenticated Encryption with Associated Data (AEAD) as its primary encryption method, which provides confidentiality, integrity, and authenticity in a single operation. The most common AEAD ciphers supported are:
ChaCha20-Poly1305
AES-128-GCM
AES-256-GCM
Shadowsocks Protocol Overview. How shadowsocks works
The principle of Shadowsocks operation: for SS programs, it is organized like a regular SOCKS5, only with the IP address 127.0.0.1. This IP is called Localhost, and the connection is made locally. That is, any program, such as a browser, connects to the same device where it is running. Then, a connection is established between the local Shadowsocks component and the server, in this bundle, the traffic is already encrypted.
You can find out more details from the video about bypassing the Great Chinese Firewall.
You can connect other applications to Shadowsocks, and the proxy will only work for selected applications. If one of them does not support a proxy, you can use, for example, Proxifier.
To install and configure Shadowsocks, you need to have some understanding of connections. What you need to start with:
- Buy and configure a VPS server in a country where the desired content is not blocked, or use a ready-made proxy server, which can be found on sites with Shadowsocks proxies.
- Client-server. There is a mobile application on Google Play, the program for PC can be downloaded for Windows and Linux.
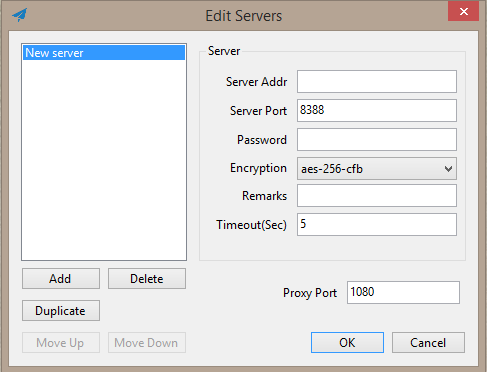
Then, simply install and launch the client, and then configure the connection to the server: add the server's IP address, port, password, and encryption method.
Shadowsocks offers three connection modes.
- Direct connection mode does not redirect your traffic through a proxy server. Preconfigured settings for some applications work in this mode.
- PAC mode: traffic will go through a proxy server when accessing blocked websites.
- In global mode, all traffic is redirected through a proxy server.
Shadowsocks can simulate an HTTPS connection to a remote server. This is necessary for traffic masking. In this case, the provider will not understand what the user is viewing and what blocks are being bypassed. This trick is possible after installing the simple-obfs traffic obfuscation plugin on the server.
Obfuscation is the masking and confusing of traffic. With its help, you can protect it from detection: the provider will not be able to find out that you are using Shadowsocks. Usually, this is achieved by encrypting the code, renaming variables into nonsense, adding unnecessary code, or simply using solutions like Cloak, Stunnel, OpenVPN Scramble, and others.
The Chinese manage to track the operation of Shadowsocks through passive traffic analysis and active "probing", and then block the connections, despite obfuscation. First, the firewall looks for possible Shadowsocks connections; and in the second stage, it connects to the servers participating in these connections, from its own IP addresses, as if it were a Shadowsocks client, and observes the server's responses.
You can read the details and mechanics of solving the problem on GitHub, but in any case, Shadowsocks still works better than VPN.
Advantages
1) Selective traffic masking. You can specify which traffic to send through the provider and which through Shadowsocks. This will help bypass blocks and maintain access to certain services simultaneously.
Example: simultaneous operation of sites like Instagram and state online services. The first may be inaccessible to your country, while the latter only work with local IP addresses. If you use VPN, you can browse Instagram, but you won't be able to access local services. However, some VPNs support separate tunneling. With Shadowsocks, you can solve this problem: you can mask Instagram traffic and use other services in parallel.
2) Protection against DPI. DPI is a traffic inspection technology for monitoring work with specific applications. Shadowsocks is hard to detect and block because it mimics a regular HTTPS connection. Therefore, the provider cannot detect "non-standard" user behavior. Nevertheless, Shadowsocks is vulnerable to active probing and pattern-analysis detection. Unlike more advanced pluggable transports (e.g., Obfs4), it can be—and has been—identified and blocked by sophisticated firewalls.
3) Reliability. Shadowsocks does not disappear even in the event of a connection failure, if the connection is configured only through it. In the event of a loss of connection to the VPN server, the traffic will go directly, and the provider will see all the information. KillSwitch partially solves this problem: the emergency button disconnects from the internet. But sometimes it does not work or there is no such function.
4) Good bandwidth. When properly configured, Shadowsocks works faster than other encryption methods, such as SSH tunneling and VPN. Approximate speed loss is no more than 3-5%.
5) Universality. There are client programs for any operating system - Windows, MacOS, Linux (various distributions), Android, and iOS.
6) Reduced computational load during encryption. From the client's point of view, this saves battery power (relevant for mobile devices), and from the server's point of view, it saves on VPS/VDS hosting for Shadowsocks.
7) Cost savings. The cheapest VPS server is suitable for Shadowsocks. Ideally, if the hosting provider provides unlimited traffic using VPS/VDS. This is much more cost-effective than a paid VPN service. You can also use other people's proxies, but options from WannaFlix, 12VPN are much more expensive than your own server, about $10 per month.
For comparison: you can rent a VPS with 5 GB of memory, 0.5 GB of RAM, and unlimited traffic for $0.87. This is sufficient for Shadowsocks. The cheapest VPN services usually cost around $2 per month, which is twice as expensive, and you need to pay for a subscription for 2-3 years upfront. Free VPNs are not considered - they transfer data, limit speed and traffic.
Disadvantages
1) Complexity of use. You need to understand how PCs and connections work, but the configuration fits in 5 lines. VPN is much easier.
2) Risk of connection speed reduction. Depending on the obfuscators used, there is a chance that Shadowsocks will significantly reduce internet speed.
3) Limited usability. Shadowsocks can be tried to change the region of Netflix, but such a scheme will not work for long: the service monitors different bypass systems. It is also not a wise solution for torrent files: if you rent a server, it is easy to find out your name and card and then accuse you of copyright infringement.
4) Limited availability. Despite the popularity of Shadowsocks, it is difficult to purchase or connect to reliable VPS servers in some regions.
5) No official audit. Many specialists have studied the open source code of Shadowsocks. But it has not undergone an official audit like OpenVPN, for example. An official audit could have been conducted by the OSTIF (Open Source Technology Improvement Fund), which was created precisely to enhance the protection of similar projects. At the same time, the code of Shadowsocks is quite simple, which creates the risk of distributing fake software packages.
Shadowsocks vs wireguard
What is Wireguard?
WireGuard is a modern VPN (Virtual Private Network) tool that helps secure your internet connection. Think of it as a private tunnel between your device (like a laptop or phone) and the internet. Anything you send or receive travels through this tunnel, so hackers or snoopers on public Wi-Fi can’t see what you’re doing. It’s designed to be:
Fast: Minimal slowdown compared to traditional VPNs.
Simple: Just install, add a “server” or “peer,” and flip a switch to connect.
Secure: Uses up-to-date encryption to keep your data safe.
You might use WireGuard when you’re on public Wi-Fi, want to appear as if you’re browsing from another country, or simply wish to keep your online activity private.
Wireguard Cryptography Suite
- Key exchange: Curve25519
- Encryption & authentication: ChaCha20-Poly1305 AEAD
- Hashing: BLAKE2s for data integrity and HMAC
Wireguard Architecture
- Single UDP port per interface, minimizing attack surface and easing firewall traversal.
- Stateless handshake using ephemeral keys: peers derive new session keys every 120 seconds (by default) without maintaining connection state.
The Difference between Shadowsocks and wireguard
Shadowsocks is ideal if you need a quick, per-app solution to bypass censorship (e.g. unblocking a website or streaming service) without touching your system’s VPN settings. WireGuard is better for full-device protection, secure site-to-site tunnels, or when you need a robust, audited VPN with minimal latency and strong cryptographic guarantees throughout your entire network stack.
Feature | Shadowsocks | WireGuard |
|---|
Type | Encrypted SOCKS5-style proxy | Layer-3 VPN tunnel |
Primary Use Case | Censorship-circumvention & per-app proxying | Site-to-site or full-device VPN |
Protocol Layer | Application layer | Network (IP) layer |
Encryption | AEAD ciphers (e.g. ChaCha20-Poly1305, AES-GCM) | Noise Protocol Framework (ChaCha20-Poly1305, Curve25519, BLAKE2s) |
Authentication | Shared secret; no built-in key exchange | Public-key cryptography with built-in key exchange |
Performance | Lightweight, user-space; modest overhead | Extremely fast, kernel (or optimized) implementation |
Detection Resistance | Can be fingerprinted by DPI unless obfuscated | Static UDP port/protocol; can be blocked but harder to DPI-fingerprint than generic VPN |
Setup & Deployment | Simple: install client, point at proxy server | Requires kernel module or supported client, root permissions, and routing config |
Routing Scope | Per-application (browser, specific app) | Entire network stack (all traffic) |
Split Tunneling | Native: only configured apps go through proxy | Needs explicit routing rules; all or defined IP ranges |
DNS Handling | Uses client’s DNS resolver | Configurable DNS settings per interface |
Shadowsocks vs OpenVPN
What is OpenVPN?
OpenVPN is a popular and trusted VPN (Virtual Private Network) technology that creates a secure, encrypted connection (often called a “tunnel”) between your device and another network over the internet. This tunnel protects your data from eavesdropping, lets you browse privately, and can make it appear as if you’re accessing the internet from a different location. OpenVPN is an open-source VPN protocol and software that implements secure point-to-point or site-to-site connections using SSL/TLS for key exchange
People use OpenVPN to:
Protect their privacy on public Wi-Fi
Access region-locked content
Securely connect to their workplace network remotely
OpenVPN Encryption: Supports robust cryptographic algorithms like AES (Advanced Encryption Standard) for data confidentiality.
OpenVPN Authentication: Uses X.509 certificates for mutual authentication, along with optional username/password and pre-shared keys.
OpenVPN Transport Protocols: Operates over UDP or TCP, allowing flexibility for different network environments and firewall traversal.
OpenVPN Tunneling: Works at the network layer (Layer 3), creating a virtual network interface (TUN) or bridging Ethernet frames (TAP).
The difference between Shadowsocks vs OpenVPN
Shadowsocks is great for lightweight, app-specific censorship circumvention with minimal latency, especially in restrictive environments.OpenVPN is a robust, well-audited VPN solution for full device or network tunneling, offering stronger security and broader use cases but with higher setup complexity and resource usage.
Feature | Shadowsocks | OpenVPN |
|---|
Type | Encrypted SOCKS5 proxy | Full-featured VPN protocol |
Primary Use | Censorship circumvention, lightweight proxy | Secure remote access, site-to-site VPNs |
Protocol Layer | Application layer proxy | Network layer VPN tunnel (Layer 3) |
Encryption | AEAD ciphers (ChaCha20-Poly1305, AES-GCM) | SSL/TLS with configurable ciphers (AES, ChaCha) |
Authentication | Pre-shared key | Certificates, username/password, or pre-shared keys |
Traffic Obfuscation | Limited by default; can use plugins for obfuscation | Can use SSL obfuscation, plus plugins like Obfsproxy |
Detection Resistance | Moderate; vulnerable to deep packet inspection unless obfuscated | Stronger out of the box; harder to block or detect |
Performance | Lightweight, low latency | Higher overhead, but stable and secure |
Ease of Setup | Simple configuration for proxy clients | More complex; requires certificate management and routing setup |
Routing Scope | Per-application proxy | Entire device or network traffic |
Use Cases | Quick censorship bypass, individual app proxy | Enterprise VPN, secure remote access, privacy |
Shadowsocks vs Shadowsocksr
What is ShadowsocksR (SSR)
Currently, Shadowsocks has a community and its own website. Therefore, enthusiasts can create their own solutions based on it. For example, after Shadowsocks was closed in 2015, another developer, breakwa11, claimed that SS is easy to detect. He created ShadowsocksR based on Shadowsocks with support for traffic obfuscation. Thus, ShadowsocksR is a branch of the original protocol, written in Python, with traffic obfuscation and detection resistance.
But more often, users recommend using the current version of Shadowsocks-Rust based on Rust.
Key points about ShadowsocksR:
Enhanced Obfuscation: SSR adds advanced traffic obfuscation methods to disguise proxy traffic, making it harder for deep packet inspection (DPI) systems—like China’s Great Firewall—to detect and block the connection.
Multiple Protocols and Obfuscation Options: Unlike Shadowsocks, which uses a relatively straightforward SOCKS5 proxy with encryption, SSR supports various protocol and obfuscation plugins that can modify packet headers, randomize traffic patterns, and evade common filtering techniques.
Backward Compatibility: SSR is mostly compatible with Shadowsocks clients but requires its own clients or compatible software for full functionality.
Not Officially Maintained: SSR is a community project with several versions maintained independently; it is not part of the official Shadowsocks repository.
Controversial: Some privacy advocates question SSR’s security and maintenance status, recommending official Shadowsocks or more modern tools like V2Ray for stronger, audited proxy solutions.
In summary, ShadowsocksR was developed to make Shadowsocks traffic harder to detect and block but is less widely used or officially supported than the original Shadowsocks today.
Shadowsocks vs SOCKS5
Shadowsocks works on SOCKS5 protocol. In simple words, it's like a your favorit app running on iOS. Shadowsocks adds more security to SOCKS5.
Here’s the difference between Shadowsocks and SOCKS5:
Aspect | SOCKS5 Proxy | Shadowsocks |
|---|
Definition | A general-purpose proxy protocol that routes network packets between client and server at the TCP level. | An encrypted proxy protocol built on top of SOCKS5 that adds strong encryption and obfuscation. |
Encryption | None by default; plain TCP forwarding | Uses AEAD encryption (e.g., ChaCha20-Poly1305), securing data in transit. |
Purpose | Simple proxy for bypassing IP blocks or routing traffic | Designed for censorship circumvention with privacy and security in mind. |
Detection Risk | High — traffic is unencrypted and easy to detect | Low — encrypts traffic and can evade deep packet inspection (DPI) with obfuscation plugins. |
Setup Complexity | Simple; supported by many clients | Requires special Shadowsocks clients or compatible software. |
Use Case | Basic proxying, accessing blocked IPs | Securely bypassing internet censorship and protecting data privacy. |
Shadowsocks vs UDP over TCP
What is UDP over TCP?
UDP over TCP refers to tunneling UDP traffic (which is connectionless and used for things like gaming, VoIP, DNS) inside TCP connections (which are connection-oriented and reliable). This is sometimes done by VPNs or proxies that only support TCP to carry UDP packets. This causes extra latency, jitter, and performance loss because TCP’s retransmission and ordering don’t fit well with UDP’s low-latency design. But it helps sometimes, because some networks or firewalls block UDP traffic or only allow TCP
Key Differences between UDP over TCP and Shadowsocks
Feature | UDP over TCP | Shadowsocks |
|---|
Traffic Type | UDP packets encapsulated inside TCP streams | Native support for both TCP and UDP traffic |
Performance | Can cause latency, packet delays, and jitter due to TCP retransmission | Optimized for minimal latency with native UDP support |
Use Case | Used when UDP is blocked or unsupported | Designed for censorship circumvention and secure proxying |
Detection Resistance | Depends on underlying TCP tunnel; generally detectable | Encrypted and obfuscated, harder to detect |
Protocol Complexity | Simple tunneling method | Complete encrypted proxy protocol with handshake and encryption |
VPN vs Shadowsocks
VPN and Shadowsocks are different tools. The first is a virtual private network, which we wrote about in our blog, and the second is a proxy protocol. Technically, they both:
- Encrypt traffic
- Help bypass blocks
But Shadowsocks assumes simpler encryption and does not allow achieving anonymity on the internet. The project was initially developed not so much for security as for bypassing the Chinese firewall. However, this problem was partially addressed in ShadowsocksR, which we will talk about at the end of the article. VPNs usually use a complex AES-256 algorithm.
VPN services often have many additional features. For example, KillSwitch. VPN is a "tunnel", so if it stops working, the traffic will go directly. In this case, it is easy to compromise the real IP address. KillSwitch protects against this: it instantly cuts off the internet connection if access to the VPN server is lost.
Finally, VPNs have a huge network of servers. You can access the internet from different countries - each time the IP address changes to the country of the selected server.
Conclusion: VPN is more convenient, safer, and easier. If you have access to it and it meets your needs, use it. If there are difficulties, then Shadowsocks should solve the problem: it works much better in countries where VPNs are blocked and restrictions are difficult to bypass. With it, data looks similar to HTTPS traffic and does not raise suspicions. Using multiple TCP connections helps achieve high speed. It is more cost-effective for simple bypassing of blocks.
Key Differences between Shadowsocks and VPN
| Shadowsocks
| VPN
|
|---|
Encryption | Weaker encryption compared to most VPNs | More reliable encryption only between your device and the server |
Access to content | Bypasses internet censorship and provides access to blocked content | Also bypasses censorship, but easier to detect |
Performance | Faster due to less encryption and shorter path to the destination point | Slower due to encryption and extra distance to the VPN server |
Configuration complexity | More difficult to configure and use for ordinary users | Relatively easy to configure and use |
Cost | Low cost or even free options | More expensive, especially for quality< PPPPPservice |
Use cases | For bypassing complex firewalls, such as in China, and accessing blocked content | For those who care about both privacy and access to blocked content |
Shadowsocks vs Mobile Proxies
What is Mobile Proxies?
Mobile proxies are actual mobile network IPs provided by cellular operators via dedicated SIM-equipped devices, offering highly trusted, dynamic, and location-specific IP addresses that are much harder to detect or block.
Comparsion table between Mobile Proxies and Shadowsocks
Aspect | Shadowsocks | Mobile Proxies |
|---|
What it is | An encrypted proxy protocol (SOCKS5-based) designed to bypass censorship by encrypting and forwarding traffic through a remote server | Actual proxies running on real mobile devices or SIM cards that use cellular networks (LTE/4G/5G) to route traffic |
Technology | Software-based proxy with encryption, runs on a VPS or server | Hardware-based proxy tied to mobile carriers, uses real mobile IP addresses assigned by cellular operators |
IP Address Type | Usually datacenter IPs, which can be flagged or blocked easily | Genuine mobile carrier IPs, highly trusted and dynamic, tied to specific geographic locations |
Detection Risk | Moderate — can be detected by deep packet inspection unless obfuscation is applied | Low — traffic appears as legitimate mobile network usage, much harder to block or flag |
Performance | Depends on server location and network; generally fast but varies | Generally fast with stable LTE/4G/5G connections; IPs rotate naturally |
Use Cases | Censorship circumvention, privacy protection, unblocking sites and services | SEO, SMM, ad verification, account creation, mobile app testing, and any use requiring highly trusted mobile IPs |
Setup | Requires installing client software and configuring proxy settings | Usually accessed via a marketplace or API; no client software needed, just proxy credentials |
Anonymity Level | Good encryption but IP can be from datacenter ranges | Very high trust and anonymity because IPs belong to mobile carriers and rotate dynamically |
What I should use Shadowsocks or Mobile Proxies?
For censorship circumvention and encrypted proxying — Shadowsocks
For authentic mobile IPs, trusted location-based access, and low detection risk, mobile proxies are superior — especially for business and automation use cases.
Conclusion
Shadowsocks is an affordable and convenient tool for bypassing blocks. It may also be useful for protecting connections. Of course, it includes fewer features than a VPN service, but it is slightly faster. However, for solving simple tasks, such as restoring access to blocked sites, it is optimal. It is easy to use and configure: there are many instructions on how to do it on the internet.
Deutsch
Español
Français
Bahasa Indonesia
Polski
Português
Русский
Українська
简体中文