Shadowsocks adalah alat gratis bagi mereka yang ingin melewati blokir dengan cara yang sederhana namun kurang populer. Ini adalah protokol jaringan dengan enkripsi data. Ini juga membantu melindungi lalu lintas dan data pribadi. Shadowsocks berbasis teknologi SOCKS5, dan kode sumbernya tersedia di GitHub.
Proyek ini dimulai pada tahun 2012. Pengembang asal Tiongkok, Clowwindy, merilis pengembangan pertama Shadowsocks di GitHub. Protokol ini membantu melewati pembatasan "Great Firewall" Tiongkok. Proyek ini menjadi populer secara global setelah dihapus dari GitHub, yang menarik perhatian media. Jurnalis menghubungkan penghapusan tersebut dengan serangan pada GitHub beberapa hari kemudian.
Clowwindy menghentikan pengembangan pada 2015 atas permintaan otoritas Tiongkok. Sejak itu, komunitas Shadowsocks yang melanjutkan pengembangan proyek ini.
Peta dari situs Freedom House menunjukkan di negara mana Shadowsocks sangat berguna.
Shadowsocks dibutuhkan untuk tugas yang mirip dengan VPN:
Dengan koneksi jaringan standar, pengguna terhubung langsung ke internet melalui penyedia layanan mereka. Misalnya, jika mereka ingin mengunjungi situs tertentu, mereka pertama-tama terhubung ke router penyedia, lalu ke situs tersebut. Jika pemerintah ingin memblokir situs ini, mereka meminta penyedia untuk memblokir akses ke alamat IP-nya.
Untuk melewati pembatasan ini, proxy digunakan. Dalam hal ini, "perantara" — server proxy — dibuat antara penyedia dan situs web. Koneksi tetap melalui penyedia, tetapi penyedia hanya tahu bahwa permintaan menuju proxy. Oleh karena itu, koneksi ke situs web tidak dibatasi, dan lalu lintas kembali ke perangkat pengguna. Namun ada beberapa masalah, misalnya:
Shadowsocks dibutuhkan untuk mengatasi masalah ini. Shadowsocks mengenkripsi muatan TCP/UDP melalui terowongan mirip SOCKS5. Untuk benar-benar meniru header HTTPS atau HTTP, diperlukan plugin obfuscation tambahan (misalnya simple-obfs, cloak). Ini mengenkripsi data dan menyajikannya sebagai lalu lintas HTML biasa. Protokol ini berbasis SOCKS5, yang kami bahas dalam artikel blog. Ini membantu melindungi koneksi melalui algoritma AEAD.
AEAD menggunakan prinsip yang sama seperti tunneling SSH, tetapi pada AEAD, data terenkripsi juga mencakup informasi tentang pengirim dan penerima. Ini menyulitkan peretas. Bahkan jika mereka mencegat pesan, mereka tidak bisa mengubah transmisi data.
Shadowsocks aman untuk melewati sensor dasar dan biasanya lebih cepat/lebih ringan dibandingkan VPN. Namun, ini bukan pengganti VPN yang diaudit sepenuhnya jika Anda membutuhkan anonimitas terjamin, resistensi anti-DPI, atau keamanan tingkat perusahaan. AEAD ("Authenticated Encryption with Associated Data") seperti AES-GCM dan ChaCha20-Poly1305 dianggap sebagai standar industri dan umumnya sangat aman. Meskipun ada diskusi di Stack Exchange yang menyatakan AEAD kurang aman, ini cukup untuk koneksi yang andal dan perlindungan data.
Shadowsocks menggunakan Authenticated Encryption with Associated Data (AEAD) sebagai metode enkripsi utama, yang memberikan kerahasiaan, integritas, dan keaslian sekaligus. Cipher AEAD yang paling umum didukung adalah:
Prinsip operasi Shadowsocks: untuk program SS, ini diorganisasi seperti SOCKS5 biasa, hanya dengan alamat IP 127.0.0.1. IP ini disebut Localhost, dan koneksi dibuat secara lokal. Artinya, program apa pun seperti browser terhubung ke perangkat yang sama tempat program berjalan. Kemudian koneksi dibuat antara komponen lokal Shadowsocks dan server, dimana lalu lintas sudah terenkripsi.
Anda dapat mengetahui lebih detail dari video tentang cara melewati Great Chinese Firewall.
Anda bisa menghubungkan aplikasi lain ke Shadowsocks, dan proxy hanya bekerja untuk aplikasi yang dipilih. Jika salah satunya tidak mendukung proxy, Anda bisa menggunakan, misalnya, Proxifier.
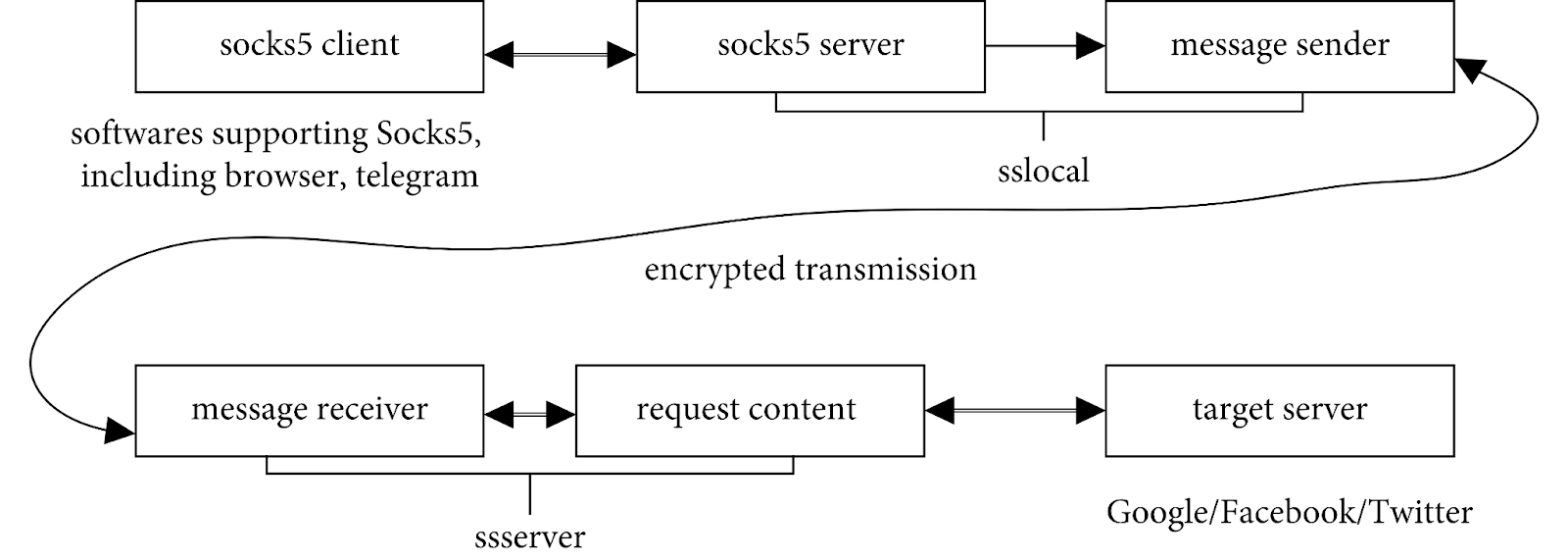
Untuk menginstal dan mengonfigurasi Shadowsocks, Anda perlu memahami koneksi. Berikut yang perlu Anda mulai:
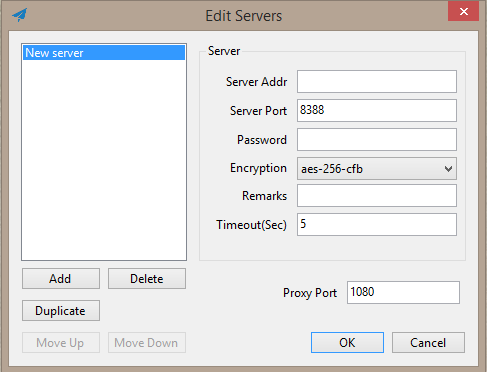
Setelah itu, cukup instal dan jalankan klien, lalu konfigurasikan koneksi ke server: tambahkan alamat IP server, port, kata sandi, dan metode enkripsi.
Shadowsocks menawarkan tiga mode koneksi.
Shadowsocks dapat meniru koneksi HTTPS ke server jarak jauh. Ini diperlukan untuk penyamaran lalu lintas. Dalam kasus ini, penyedia tidak akan mengerti apa yang dilihat pengguna dan blok apa yang dilewati. Trik ini memungkinkan setelah memasang plugin obfuscation simple-obfs di server.
Obfuscation adalah penyamaran dan pengacauan lalu lintas. Dengan ini, Anda bisa melindunginya dari deteksi: penyedia tidak akan mengetahui bahwa Anda menggunakan Shadowsocks. Biasanya, ini dicapai dengan mengenkripsi kode, mengganti nama variabel menjadi tidak berarti, menambahkan kode yang tidak perlu, atau menggunakan solusi seperti Cloak, Stunnel, OpenVPN Scramble, dan lainnya.
Pihak Tiongkok dapat melacak operasi Shadowsocks melalui analisis lalu lintas pasif dan "probing" aktif, kemudian memblokir koneksi meskipun ada obfuscation. Pertama, firewall mencari koneksi Shadowsocks yang mungkin; pada tahap kedua, firewall menyambung ke server dari alamat IP-nya sendiri seolah-olah menjadi klien Shadowsocks dan mengamati respons server.
Anda dapat membaca detail dan mekanisme solusi masalah di GitHub, tapi dalam hal apapun Shadowsocks tetap bekerja lebih baik daripada VPN.
1) Penyembunyian lalu lintas selektif. Anda dapat menentukan lalu lintas mana yang dikirim melalui penyedia dan mana yang melalui Shadowsocks. Ini membantu melewati blokir dan mempertahankan akses ke layanan tertentu secara bersamaan.
Contoh: penggunaan bersamaan situs seperti Instagram dan layanan online negara. Instagram mungkin tidak dapat diakses dari negara Anda, sementara layanan negara hanya berfungsi dengan IP lokal. Jika menggunakan VPN, Anda bisa menjelajah Instagram, tapi tidak bisa mengakses layanan lokal. Beberapa VPN mendukung tunneling terpisah. Dengan Shadowsocks, Anda bisa menyelesaikan masalah ini: Anda bisa menyembunyikan lalu lintas Instagram dan menggunakan layanan lain secara paralel.
2) Perlindungan terhadap DPI. DPI adalah teknologi inspeksi paket dalam untuk memantau penggunaan aplikasi tertentu. Shadowsocks sulit dideteksi dan diblokir karena meniru koneksi HTTPS biasa. Namun, Shadowsocks rentan terhadap probing aktif dan deteksi pola. Tidak seperti transportasi pluggable yang lebih canggih (misalnya Obfs4), Shadowsocks bisa dan pernah dikenali serta diblokir oleh firewall canggih.
3) Keandalan. Shadowsocks tidak hilang walau koneksi terputus, jika koneksi hanya melalui Shadowsocks. Jika koneksi ke server VPN hilang, lalu lintas akan langsung berjalan dan penyedia bisa melihat semua informasi. KillSwitch sebagian menyelesaikan masalah ini: tombol darurat memutus internet jika akses ke server VPN hilang. Namun terkadang tidak bekerja atau fitur ini tidak tersedia.
4) Bandwidth baik. Dengan konfigurasi yang tepat, Shadowsocks bekerja lebih cepat daripada metode enkripsi lain seperti tunneling SSH dan VPN. Kehilangan kecepatan sekitar 3–5%.
5) Universalitas. Ada program klien untuk semua sistem operasi - Windows, MacOS, Linux (berbagai distro), Android, dan iOS.
6) Beban komputasi rendah saat enkripsi. Dari sisi klien, ini menghemat baterai (penting untuk perangkat mobile), dan dari sisi server, menghemat VPS/VDS hosting untuk Shadowsocks.
7) Penghematan biaya. VPS termurah cocok untuk Shadowsocks. Ideal jika penyedia hosting menyediakan trafik tanpa batas menggunakan VPS/VDS. Ini jauh lebih hemat biaya dibandingkan layanan VPN berbayar. Anda juga bisa menggunakan proxy orang lain, tapi opsi dari WannaFlix, 12VPN jauh lebih mahal dibanding server sendiri, sekitar $10 per bulan.
Untuk perbandingan: Anda bisa menyewa VPS dengan 5 GB memori, 0,5 GB RAM, dan trafik tak terbatas dengan harga $0,87. Ini cukup untuk Shadowsocks. Layanan VPN termurah biasanya sekitar $2 per bulan, dua kali lebih mahal, dan Anda perlu membayar langganan 2–3 tahun sekaligus. VPN gratis tidak diperhitungkan - mereka membatasi data, kecepatan dan trafik.
1) Kompleksitas penggunaan. Anda perlu memahami cara kerja PC dan koneksi, meskipun konfigurasi hanya beberapa baris. VPN jauh lebih mudah.
2) Risiko penurunan kecepatan koneksi. Tergantung obfuscator yang digunakan, Shadowsocks bisa menurunkan kecepatan internet secara signifikan.
3) Keterbatasan penggunaan. Shadowsocks bisa dicoba untuk mengubah wilayah Netflix, tapi cara ini tidak bertahan lama karena layanan memantau sistem bypass. Ini juga bukan solusi bijak untuk torrent: jika menyewa server, mudah dilacak nama dan kartu Anda lalu dituduh pelanggaran hak cipta.
4) Keterbatasan ketersediaan. Meskipun populer, sulit membeli atau menghubungkan VPS server yang andal di beberapa wilayah.
5) Tidak ada audit resmi. Banyak ahli memeriksa kode sumber terbuka Shadowsocks. Namun belum ada audit resmi seperti OpenVPN. Audit resmi bisa dilakukan oleh OSTIF, yang dibuat untuk meningkatkan keamanan proyek semacam ini. Namun kode Shadowsocks cukup sederhana, yang berisiko menyebarkan paket perangkat lunak palsu.
WireGuard adalah alat VPN modern yang membantu mengamankan koneksi internet Anda. Bayangkan sebagai terowongan pribadi antara perangkat Anda (laptop atau ponsel) dan internet. Apa pun yang Anda kirim atau terima melewati terowongan ini, jadi hacker atau penyadap di Wi-Fi umum tidak bisa melihat aktivitas Anda. WireGuard dirancang agar:
Anda bisa menggunakan WireGuard saat di Wi-Fi umum, ingin terlihat seperti browsing dari negara lain, atau hanya ingin menjaga privasi online.
Shadowsocks ideal jika Anda membutuhkan solusi cepat, per-app untuk melewati sensor (misalnya membuka situs atau layanan streaming) tanpa mengubah pengaturan VPN sistem Anda. WireGuard lebih baik untuk perlindungan perangkat penuh, terowongan site-to-site yang aman, atau saat Anda memerlukan VPN yang kuat, diaudit, dengan latensi minimal dan jaminan kriptografi kuat di seluruh jaringan.
Fitur | Shadowsocks | WireGuard |
|---|---|---|
Jenis | Proxy terenkripsi bergaya SOCKS5 | Terowongan VPN Layer-3 |
Kegunaan utama | Penghindaran sensor & proxy per aplikasi | VPN site-to-site atau seluruh perangkat |
Lapisan protokol | Lapisan aplikasi | Lapisan jaringan (IP) |
Enkripsi | AEAD (misal ChaCha20-Poly1305, AES-GCM) | Noise Protocol Framework (ChaCha20-Poly1305, Curve25519, BLAKE2s) |
Autentikasi | Kunci rahasia bersama; tanpa pertukaran kunci bawaan | Kryptografi kunci publik dengan pertukaran kunci bawaan |
Kinerja | Ringan, di user-space; overhead rendah | Sangat cepat, implementasi kernel/teroptimasi |
Perlindungan deteksi | Dapat dikenali oleh DPI kecuali ada obfuscation | Port/protokol UDP statis; lebih sulit dideteksi dibanding VPN umum |
Setup & penyebaran | Mudah: instal klien, arahkan ke proxy server | Perlu modul kernel atau klien yang didukung, hak root, dan konfigurasi routing |
Ruang lingkup routing | Per aplikasi (browser, aplikasi spesifik) | Seluruh tumpukan jaringan (semua lalu lintas) |
OpenVPN adalah teknologi VPN populer dan terpercaya yang membuat koneksi aman dan terenkripsi (sering disebut “terowongan”) antara perangkat Anda dan jaringan lain melalui internet. Terowongan ini melindungi data Anda dari penyadapan, memungkinkan Anda browsing secara privat, dan bisa membuat Anda terlihat seolah-olah mengakses internet dari lokasi berbeda. OpenVPN adalah protokol dan perangkat lunak VPN sumber terbuka yang menggunakan SSL/TLS untuk pertukaran kunci dalam koneksi point-to-point atau site-to-site yang aman.
Orang menggunakan OpenVPN untuk:
Enkripsi OpenVPN: Mendukung algoritma kriptografi kuat seperti AES untuk kerahasiaan data.
Autentikasi OpenVPN: Menggunakan sertifikat X.509 untuk autentikasi mutual, bersama dengan username/password dan kunci pra-bagi opsional.
Protokol transport OpenVPN: Beroperasi lewat UDP atau TCP, memberikan fleksibilitas untuk berbagai lingkungan jaringan dan melewati firewall.
Tunneling OpenVPN: Beroperasi di lapisan jaringan (Layer 3), membuat interface jaringan virtual (TUN) atau bridging frame Ethernet (TAP).
Shadowsocks sangat cocok untuk penghindaran sensor ringan, khusus aplikasi dengan latensi minimal, terutama di lingkungan yang ketat. OpenVPN adalah solusi VPN yang kuat dan telah diaudit untuk tunneling seluruh perangkat atau jaringan, menawarkan keamanan lebih tinggi dan cakupan penggunaan yang lebih luas, namun dengan setup yang lebih rumit dan penggunaan sumber daya yang lebih besar.
Fitur | Shadowsocks | OpenVPN |
|---|---|---|
Jenis | Proxy SOCKS5 terenkripsi | Protokol VPN lengkap |
Penggunaan utama | Penghindaran sensor, proxy ringan | Akses jarak jauh aman, VPN site-to-site |
Lapisan protokol | Proxy lapisan aplikasi | Terowongan VPN lapisan jaringan (Layer 3) |
Enkripsi | AEAD (ChaCha20-Poly1305, AES-GCM) | SSL/TLS dengan cipher yang dapat dikonfigurasi (AES, ChaCha) |
Autentikasi | Kunci pra-bagi | Sertifikat, username/password, atau kunci pra-bagi |
Obfuscation lalu lintas | Terbatas secara default; dapat menggunakan plugin obfuscation | Dapat menggunakan obfuscation SSL, plus plugin seperti Obfsproxy |
Perlindungan deteksi | Sedang; rentan terhadap inspeksi paket dalam kecuali obfuscation | Lebih kuat dari awal; lebih sulit diblokir atau dideteksi |
Kinerja | Ringan, latensi rendah | Overhead lebih tinggi, tapi stabil dan aman |
Mudah pengaturan | Konfigurasi mudah untuk klien proxy | Lebih kompleks; butuh manajemen sertifikat dan konfigurasi routing |
Ruang lingkup routing | Proxy per aplikasi | Seluruh perangkat atau lalu lintas jaringan |
Kegunaan | Bypass sensor cepat, proxy aplikasi individual | VPN perusahaan, akses jarak jauh aman, privasi |
Saat ini, Shadowsocks memiliki komunitas dan situs web sendiri. Oleh karena itu, penggemar dapat membuat solusi berdasarkan itu. Misalnya, setelah Shadowsocks ditutup pada 2015, pengembang lain, breakwa11, menyatakan bahwa SS mudah dideteksi. Dia membuat ShadowsocksR berdasarkan Shadowsocks dengan dukungan obfuscation lalu lintas. Jadi, ShadowsocksR adalah cabang protokol asli, ditulis dalam Python, dengan obfuscation lalu lintas dan resistensi deteksi.
Namun, lebih sering disarankan menggunakan versi terbaru Shadowsocks-Rust yang berbasis Rust.
Poin utama tentang ShadowsocksR:
Singkatnya, ShadowsocksR dikembangkan untuk membuat lalu lintas Shadowsocks lebih sulit dideteksi dan diblokir tetapi sekarang kurang digunakan dan tidak didukung resmi dibandingkan Shadowsocks asli.
Shadowsocks bekerja pada protokol SOCKS5. Sederhananya, seperti aplikasi favorit Anda yang berjalan di iOS. Shadowsocks menambahkan keamanan lebih pada SOCKS5.
Berikut perbedaan antara Shadowsocks dan SOCKS5:
Aspek | Proxy SOCKS5 | Shadowsocks |
|---|---|---|
Definisi | Protokol proxy umum yang mengarahkan paket jaringan antara klien dan server pada tingkat TCP. | Protokol proxy terenkripsi yang dibangun di atas SOCKS5 dengan enkripsi kuat dan obfuscation. |
Enkripsi | Tidak ada secara default; pengiriman TCP biasa | Menggunakan enkripsi AEAD (misal ChaCha20-Poly1305), melindungi data selama transit. |
Tujuan | Proxy sederhana untuk melewati blokir IP atau mengarahkan lalu lintas | Dirancang untuk melewati sensor dengan privasi dan keamanan. |
Risiko deteksi | Tinggi — lalu lintas tidak terenkripsi dan mudah dideteksi | Rendah — mengenkripsi lalu lintas dan dapat menghindari inspeksi paket dalam (DPI) dengan plugin obfuscation. |
Kompleksitas setup | Sederhana; didukung oleh banyak klien | Membutuhkan klien Shadowsocks khusus atau perangkat lunak kompatibel. |
Penggunaan | Proxy dasar, mengakses IP yang diblokir | Melewati sensor internet dengan aman dan melindungi privasi data. |
UDP over TCP mengacu pada tunneling lalu lintas UDP (yang connectionless dan digunakan untuk hal seperti game, VoIP, DNS) di dalam koneksi TCP (yang connection-oriented dan andal). Ini kadang dilakukan oleh VPN atau proxy yang hanya mendukung TCP untuk mengangkut paket UDP. Ini menyebabkan latensi ekstra, jitter, dan penurunan performa karena retransmisi dan pengurutan TCP tidak cocok dengan desain UDP yang rendah latensi. Namun kadang berguna karena beberapa jaringan atau firewall memblokir UDP atau hanya mengizinkan TCP.
Fitur | UDP over TCP | Shadowsocks |
|---|---|---|
Jenis lalu lintas | Paket UDP dikapsulkan dalam aliran TCP | Dukungan native untuk lalu lintas TCP dan UDP |
Performa | Dapat menyebabkan latensi, delay paket, dan jitter karena retransmisi TCP | Dioptimalkan untuk latensi minimal dengan dukungan UDP native |
Kasus penggunaan | Digunakan ketika UDP diblokir atau tidak didukung | Dirancang untuk penghindaran sensor dan proxy aman |
Perlindungan deteksi | Tergantung pada terowongan TCP dasar; umumnya dapat dideteksi | Terenkripsi dan diobfuscate, lebih sulit dideteksi |
Kompleksitas protokol | Metode tunneling sederhana | Protokol proxy terenkripsi lengkap dengan handshake dan enkripsi |
VPN dan Shadowsocks adalah alat berbeda. Yang pertama adalah jaringan pribadi virtual yang kami bahas di blog, yang kedua adalah protokol proxy. Secara teknis, keduanya:
Tetapi Shadowsocks menggunakan enkripsi lebih sederhana dan tidak memungkinkan anonimitas di internet. Proyek ini awalnya dibuat bukan untuk keamanan, melainkan untuk melewati firewall Tiongkok. Namun, masalah ini sebagian diatasi di ShadowsocksR yang akan kami bahas di akhir artikel. VPN biasanya menggunakan algoritma AES-256 yang kompleks.
Layanan VPN sering memiliki banyak fitur tambahan, seperti KillSwitch. VPN adalah "terowongan", jadi jika berhenti berfungsi, lalu lintas akan langsung berjalan dan IP asli dapat terbuka. KillSwitch mencegah ini dengan memutus koneksi internet jika akses ke server VPN hilang.
Akhirnya, VPN memiliki jaringan server besar. Anda bisa mengakses internet dari berbagai negara – alamat IP berubah ke negara server yang dipilih.
Kesimpulan: VPN lebih nyaman, aman, dan mudah digunakan. Jika tersedia dan sesuai kebutuhan, gunakan VPN. Jika ada kesulitan, Shadowsocks menyelesaikan masalah: lebih baik di negara yang VPN-nya diblokir dan ada pembatasan ketat. Dengan Shadowsocks, data tampak seperti lalu lintas HTTPS dan tidak menimbulkan kecurigaan. Penggunaan banyak koneksi TCP membantu kecepatan tinggi. Ini lebih hemat biaya untuk bypass sederhana.
Shadowsocks | VPN | |
|---|---|---|
Enkripsi | Enkripsi lebih lemah dibanding sebagian besar VPN | Enkripsi lebih andal antara perangkat dan server |
Akses konten | Melewati sensor internet dan mengakses konten diblokir | Juga melewati sensor, tapi lebih mudah dideteksi |
Kinerja | Lebih cepat karena enkripsi lebih sedikit dan jalur lebih pendek | Lebih lambat karena enkripsi dan jarak ke server VPN |
Kompleksitas konfigurasi | Lebih sulit dikonfigurasi dan digunakan oleh pengguna biasa | Relatif mudah dikonfigurasi dan digunakan |
Biaya | Biaya rendah atau bahkan gratis | Lebih mahal, terutama untuk layanan berkualitas |
Kasus penggunaan | Untuk melewati firewall kompleks (misalnya di Tiongkok) dan akses konten blokir | Untuk pengguna yang mengutamakan privasi dan akses konten blokir |
Mobile proxies adalah IP jaringan seluler asli yang disediakan oleh operator seluler melalui perangkat khusus dengan SIM card, menawarkan IP yang sangat dipercaya, dinamis, dan terkait lokasi yang jauh lebih sulit dideteksi atau diblokir.
Aspek | Shadowsocks | Mobile Proxies |
|---|---|---|
Apa itu | Protokol proxy terenkripsi (berbasis SOCKS5) yang dirancang untuk melewati sensor dengan mengenkripsi dan meneruskan lalu lintas melalui server jarak jauh | Proxy nyata yang berjalan di perangkat mobile atau kartu SIM yang menggunakan jaringan seluler (LTE/4G/5G) untuk mengarahkan lalu lintas |
Teknologi | Proxy berbasis perangkat lunak dengan enkripsi, berjalan di VPS atau server | Proxy berbasis perangkat keras yang terikat pada operator seluler, menggunakan IP mobile asli yang diberikan operator seluler |
Jenis alamat IP | Biasanya IP pusat data yang mudah diblokir atau diberi tanda | IP asli operator seluler, sangat dipercaya dan dinamis, terkait lokasi geografis tertentu |
Risiko deteksi | Sedang — dapat dideteksi oleh inspeksi paket dalam kecuali ada obfuscation | Rendah — lalu lintas terlihat seperti penggunaan jaringan seluler yang sah, sulit diblokir atau diberi tanda |
Kinerja | Tergantung lokasi server dan jaringan; umumnya cepat tetapi bervariasi | Umumnya cepat dengan koneksi LTE/4G/5G stabil; IP berputar secara alami |
Kasus penggunaan | Melewati sensor, perlindungan privasi, membuka blokir situs dan layanan | SEO, SMM, verifikasi iklan, pembuatan akun, pengujian aplikasi mobile, dan penggunaan yang memerlukan IP mobile yang sangat dipercaya |
Pengaturan | Membutuhkan instalasi perangkat lunak klien dan konfigurasi proxy | Biasanya diakses melalui marketplace atau API; tidak perlu perangkat lunak klien, cukup kredensial proxy |
Tingkat anonimitas | Enkripsi baik tapi IP bisa dari rentang pusat data | Kepercayaan dan anonimitas sangat tinggi karena IP milik operator seluler dan berputar dinamis |
Untuk melewati sensor dan proxy terenkripsi — gunakan Shadowsocks.
Untuk IP mobile asli, akses berbasis lokasi yang terpercaya, dan risiko deteksi rendah, mobile proxies lebih unggul — terutama untuk bisnis dan otomatisasi.
Shadowsocks adalah alat yang terjangkau dan nyaman untuk melewati blokir. Ini juga bisa berguna untuk melindungi koneksi. Tentu, ia memiliki fitur lebih sedikit dibanding layanan VPN, tapi sedikit lebih cepat. Namun untuk tugas sederhana seperti mengembalikan akses ke situs yang diblokir, ini optimal. Mudah digunakan dan dikonfigurasi; banyak panduan tersedia di internet.