A SOCKS5 proxy server for routing your traffic can increase anonymity and speed. But not security, as it operates without data encryption. SOCKS is a basic Internet proxy protocol that operates over TCP and, in its version 5, also supports UDP. SOCKS5 is the latest and most widely used version of the protocol. In this article, we will explain what this proxy server is, reveal its advantages and areas of application.
What is a SOCKS proxy?
Socks proxy is a proxy that transmits data using the Socket Secure protocol. It helps to ensure secure communication that is transparent to the user. These proxies route traffic through the firewall and facilitate communication with the server. At the same time, the proxy does not make any changes to the data: the traffic is redirected in its original form. Thus, websites do not see the client's real IP address and the fact that they are using a proxy.
At the same time, Socks proxies:
- Are perfect for all types of protocols and data, that is, not only for browsers, but for all programs that do not directly use a proxy (ports 1080 and 1081).
- Do not encrypt traffic, so be careful if you are transmitting confidential data. But this issue can be solved, we will explain further.
- Offer different types of authentication.
- Are good for bypassing restrictions, they have stable and fast connections, which is useful for streaming media, P2P, and online games.
And be more careful if you are working with free Socks servers. They have a higher risk of data leaks and increased advertising. We have already compared them with paid ones in our article "Paid vs Free Proxies: Which Ones to Choose".
Types of Authentication
Authentication is a way to verify identity when connecting to a proxy. With authentication, access to the proxy is restricted to authorised users and your data is slightly better protected. In web-scraping scenarios, authentication can also lower the risk of IP bans. In other words, SOCKS5 proxy servers are safer for connections than the HTTP protocol.
SOCKS5 offers three types of authentication:
- Null - no authentication is required to connect to the proxy server.
- Username and password authentication - you need to enter login credentials to access the system and connect to the proxy server. Logins and passwords help limit the number of proxy users.
- Whitelisted IP - you can set a list of IPs which be allowed for connection to the proxy
What is SOCKS5?
There are two generations of Socks proxies:
- SOCKS4 does not support IPv6, authentication, or remote DNS; it supports only TCP connections.
- SOCKS supports both IPv4 and IPv6, multiple authentication methods, such as login and password authentication, handles remote DNS requests, TCP and UDP connections, SSH tunneling methodology for traffic relay.
In many contexts “SOCKS” is used as shorthand for SOCKS5, but the version should be stated when precision matters. Both terms can be used interchangeably.
SOCKS proxies can be used for the same purposes as HTTP proxies. For example, to increase download speed to route traffic or bypass blocking, and maintain confidentiality while working on the network.
SOCKS5 is suitable for working outside the browser. The protocol operates at the session level - the 5th level in the OSI model. This means that the protocol allows forwarding of arbitrary TCP (and, in SOCKS5, UDP) traffic, adding only a small SOCKS header.
The OSI model describes how different network protocols interact across seven conceptual layers and the coordination of the operation of different devices. It shows the stages of data transmission from the program to the cable.
It looks like this:
Host levels in the OSI model
Level | Data Type | Functions | Examples |
7. Application | Data | Access to network services | HTTP, FTP, POP3, SMTP, WebSocket |
6. Presentation | Data | Data representation and encryption | ASCII, EBCDIC, JPEG, MIDI |
5. Session | Data | Session control | SOCKS5, RPC, PAP, L2TP, gRPC |
4. Transport | Segments and datagrams | Direct communication between endpoints and reliability | TCP, UDP, SCTP, Ports |
3. Network | Packets | Route determination and logical addressing | IPv4, IPv6, IPsec, AppleTalk, ICMP |
2. Data Link | Bits and frames | Physical addressing | PPP, IEEE 802.22, Ethernet, DSL, ARP, network card |
1. Physical | Bits | Working with transmission media, signals, and binary data | USB, RJ (twisted pair, coaxial, fiber optic), radio channel |
However, SOCKS5 does not provide built-in encryption. Therefore, any intermediary on the route can see your traffic. But there is a plus - the data transmission speed is the highest among all proxy protocols and even faster than VPN.
Can security be increased?
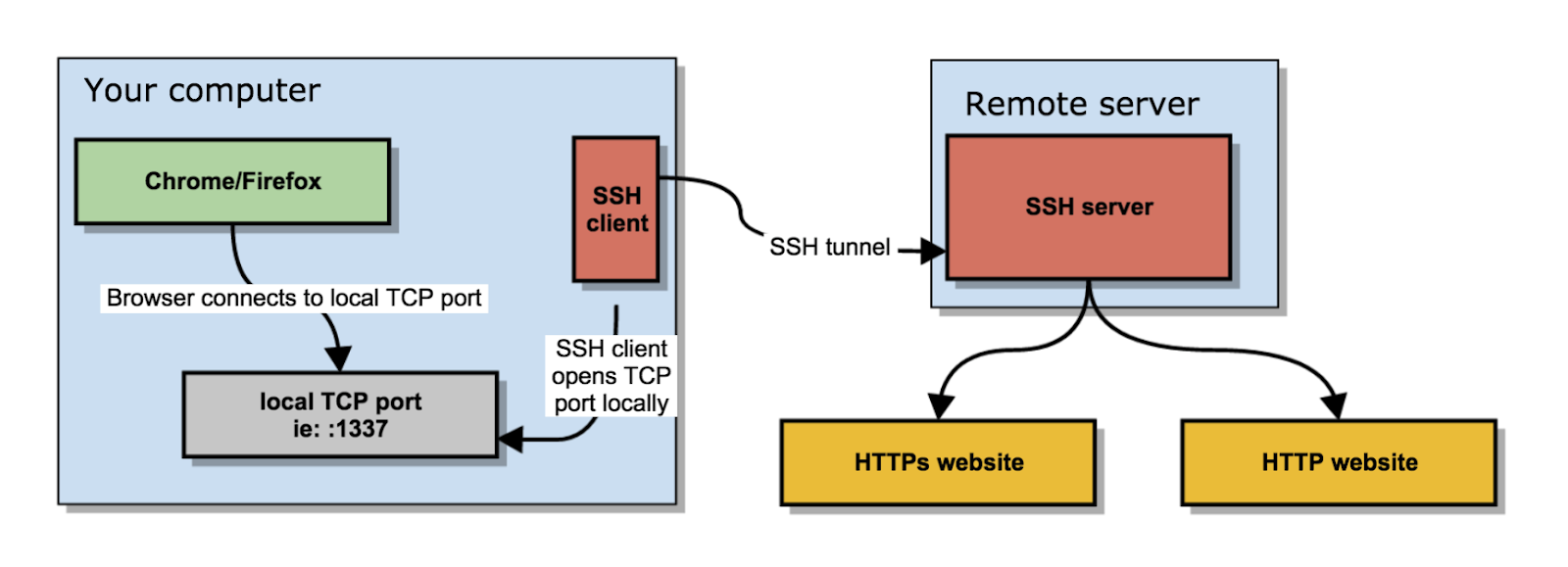
Dedicated (not shared) SOCKS5 proxy servers can be configured for increased protection, like VPN servers, but only if you manually set up an encrypted SSH tunnel (Secure Shell Protocol). The traffic will then go through the remote server. Do not confuse this with SSL/TLS encryption. In essence, you can create a local proxy yourself using the PuTTY utility.
Thanks to SSH, all traffic, including SOCKS5 traffic, can be directed from the client through a private encrypted SSH tunnel to a remote SSH server. This can help you hide traffic and bypass more advanced (L7-DPI) firewalls. However, advanced configuration skills are required for this. Schematically, the connection will look like this:
You can increase your SOCKS5 proxy using mobile proxy
Mobile SOCKS5 proxy operates on private dedicated mobile device and using mobile internet with high-trusted IP. It helps you to save anonymity, privacy and looks like real user at the same time. Private channel keeps your data safe.
TCP and UDP
Earlier versions, such as SOCKS4, supported only TCP., while SOCKS5 proxies handle UDP traffic as well. Therefore, we recommend using SOCKS5 as it is more versatile.
- TCP is a protocol for ensuring message delivery between the client and server. It is necessary for connection reliability. TCP is best suited for precise data delivery, such as documents, websites content and messaging.
- UDP, on the other hand, does not guarantee delivery, and this protocol is packet-based, which helps to transmit traffic faster without spending time on retransmissions. UDP is best suited for P2P traffic, voice transmission, and streaming video.
These protocols complement each other well.
If the client exchanges TCP data, SOCKS forwards the data over the established connection. If the client exchanges UDP data, it may be necessary to use a TCP connection to establish initial communication, as UDP itself can only send data. After that, TCP is only needed for successful responses from the SOCKS5 proxy server and instructions for sending UDP packets. More details about the differences between protocols can be found in the article on Spiceworks.
Advantages of SOCKS5
You can configure SOCKS5 proxies at the application level or via a system-wide proxy setting. SOCKS5 can be applied at the application level. This means you can choose which programs will route traffic through this proxy. This is important if you only need to enable the proxy server for one application. SOCKS proxies are usually used in browsers or file-sharing P2P clients, such as BitTorrent.
For regular downloading, uploading, and content transfer, SOCKS proxies are the best option, as they stand out in the following ways:
- Bypassing restrictions. SOCKS5 is one of the best ways to bypass website blocking. This is useful if your IP address or SOCKS5 IP has been blacklisted.
- Speed and connection stability. Previous versions of SOCKS only used TCP for uninterrupted and reliable data transmission. SOCKS5 works with the UDP protocol, which improves speed.
- Performance. Unlike other types of proxies, SOCKS does not interfere with data packets. There are fewer errors during transmission.
What is SOCKS5 Proxy Used For
They are suitable for typical tasks that other proxy options can handle. However, they show greater efficiency in the following scenarios:
- Scraping and SEO - such tasks with high traffic are suitable. For example, a dynamic IPv6 proxy server will help you stay undetected when scraping, protection technology and provide effective and fast results. Of course, data can be collected using HTTP proxies, but SOCKS5 allows parsing data from any connection - TCP or UDP - and from different sources such as video streams, VoIP calls, etc.
- Anonymous connections, if you need to mask the real IP address.
- Online games, video and voice chats.
- P2P and torrents. Here, high protocol speed between nodes and masking of the real IP address will be required.
- Access to MySQL databases, LDAP services.
The main problem with SOCKS5 is the lack of data encryption. This can lead to:
- Hacking. We do not recommend working with confidential data when using SOCKS5. When passing through a third-party server, hackers can steal personal information in an instant.
- Intrusive advertising and viruses. Public proxy servers often earn money by sending advertisements to connected users. These ads and pop-ups not only annoy, but can also pose a threat in the form of malware that sends data to hackers.
- Insecurity in the network. When connecting to a Socks proxy server, you share your personal data, such as the host name, with strangers. Your identifier can be used for malicious purposes or sold on the darknet.
To avoid these problems, you should use only private dedicated paid proxies. If you want get the highest level of anonymity and truthfulness, you should use mobile proxies.
Deutsch
Español
Français
Bahasa Indonesia
Polski
Português
Русский
Українська
简体中文