Was ist Shadowsocks?
Shadowsocks ist ein kostenloses Tool für diejenigen, die auf einfache, aber weniger bekannte Weise Blockaden umgehen möchten. Es handelt sich um ein Netzwerkprotokoll mit Datenverschlüsselung. Es hilft auch, den Datenverkehr und persönliche Daten zu schützen. Es basiert auf SOCKS5-Technologien, und der Quellcode ist auf GitHub verfügbar.
Das Projekt begann 2012. Der chinesische Entwickler Clowwindy veröffentlichte die ersten Entwicklungen von Shadowsocks auf GitHub. Das Protokoll half, die Beschränkungen der „Großen Firewall“ Chinas zu umgehen. Das Projekt wurde weltweit bekannt, nachdem es von GitHub entfernt wurde, was die Aufmerksamkeit der Medien auf sich zog. Journalisten vermuteten einen Zusammenhang zwischen der Entfernung und dem Angriff auf GitHub, der einige Tage später stattfand.
Clowwindy stellte die Entwicklung 2015 auf Anweisung der chinesischen Behörden ein. Seitdem wird das Projekt von der Shadowsocks-Community weiterentwickelt.
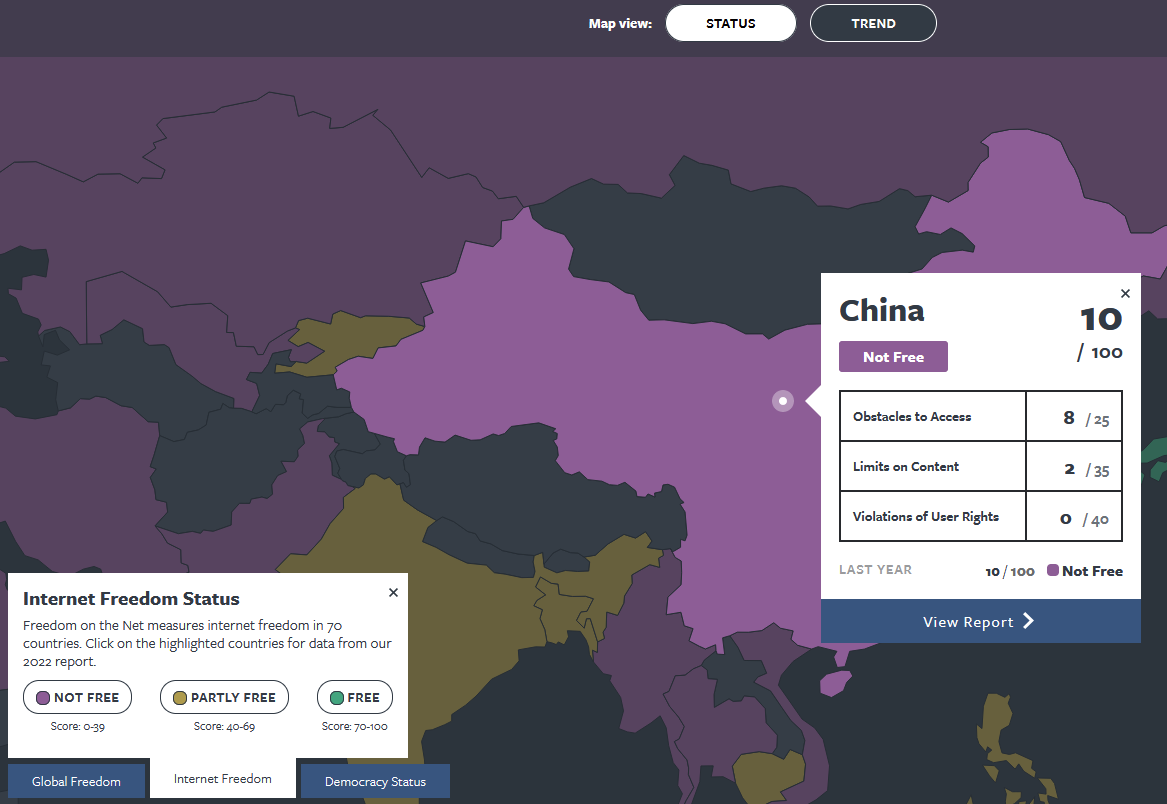
Die Karte von der Freedom House Website zeigt, in welchen Ländern Shadowsocks definitiv nützlich ist.
Shadowsocks wird für ähnliche Aufgaben wie VPN benötigt:
- Blockaden umgehen. Protokolle werden verwendet, um auf gesperrte Ressourcen sowohl im Land als auch von Providern und Betreibern zuzugreifen.
- Schutz persönlicher Daten. Es ist schwieriger, auf den Datenverkehr und persönliche Daten zuzugreifen.
- Sichere Verbindung von ungeschützten Punkten – zum Beispiel über kostenloses WLAN.
Wie funktioniert Shadowsocks? Protokollerklärung
Bei einer normalen Netzwerkverbindung verbindet sich der Benutzer direkt über seinen Anbieter mit dem Internet. Wenn er beispielsweise eine bestimmte Website besuchen möchte, verbindet er sich zunächst mit dem Router des Anbieters und dann mit der Website selbst. Wenn der Staat diese Website blockieren möchte, fordert er den Anbieter auf, den Zugriff auf die IP-Adresse zu blockieren.
Um diese Einschränkung zu umgehen, werden Proxys verwendet. In diesem Fall wird ein „Vermittler“ – ein Proxy-Server – zwischen Anbieter und Website geschaltet. Die Verbindung läuft weiterhin über den Anbieter, der jedoch nur weiß, dass die Anfrage an den Proxy geht. Daher ist die Verbindung zur Website unbeschränkt und der Datenverkehr wird zurück zum Gerät des Nutzers geleitet. Es gibt jedoch einige Probleme, zum Beispiel:
- Websites und Anbieter können erkennen, dass Sie Umgehungswerkzeuge verwenden.
- Die Verbindung ist nicht sicher. Sie können jedoch einen Proxy mit Verschlüsselung oder ein VPN verwenden, die den Datenverkehr meist verschlüsseln.
Shadowsocks löst diese Probleme. Shadowsocks verschlüsselt TCP/UDP-Nutzlasten über einen SOCKS5-ähnlichen Tunnel. Um HTTPS- oder HTTP-Header wirklich zu imitieren, ist ein zusätzliches Obfuskations-Plugin (z. B. simple-obfs, cloak) erforderlich. Es verschlüsselt Daten und präsentiert sie als normalen HTML-Verkehr. Das Protokoll basiert auf SOCKS5, zu dem wir einen Blogartikel haben. Es schützt die Verbindung durch den AEAD-Algorithmus.
AEAD verwendet dasselbe Prinzip wie SSH-Tunneling, aber bei AEAD enthalten die verschlüsselten Daten auch Informationen über Absender und Empfänger. Das erschwert Hackern das Leben. Selbst wenn sie eine Nachricht abfangen, können sie die Datenübertragung nicht manipulieren.
Ist Shadowsocks sicher?
Shadowsocks ist sicher für grundlegendes Umgehen von Zensur und normalerweise schneller/leichter als ein VPN. Es ist jedoch kein Ersatz für ein vollständig geprüftes VPN, wenn Sie garantierte Anonymität, Anti-DPI-Widerstand oder unternehmensgerechte Sicherheit benötigen. AEAD-Modi („Authenticated Encryption with Associated Data“) wie AES-GCM und ChaCha20-Poly1305 gelten allgemein als sehr sicher. Obwohl es Diskussionen auf Stack Exchange gibt, die AEAD als weniger sicher ansehen, ist es für eine zuverlässige Verbindung und den Schutz der Daten ausreichend.
Verschlüsselungsmethode von Shadowsocks
Shadowsocks verwendet Authenticated Encryption with Associated Data (AEAD) als primäre Verschlüsselungsmethode, die Vertraulichkeit, Integrität und Authentizität in einem Schritt bietet. Die am häufigsten unterstützten AEAD-Chiffren sind:
- ChaCha20-Poly1305
- AES-128-GCM
- AES-256-GCM
Überblick über das Shadowsocks-Protokoll. Wie Shadowsocks funktioniert
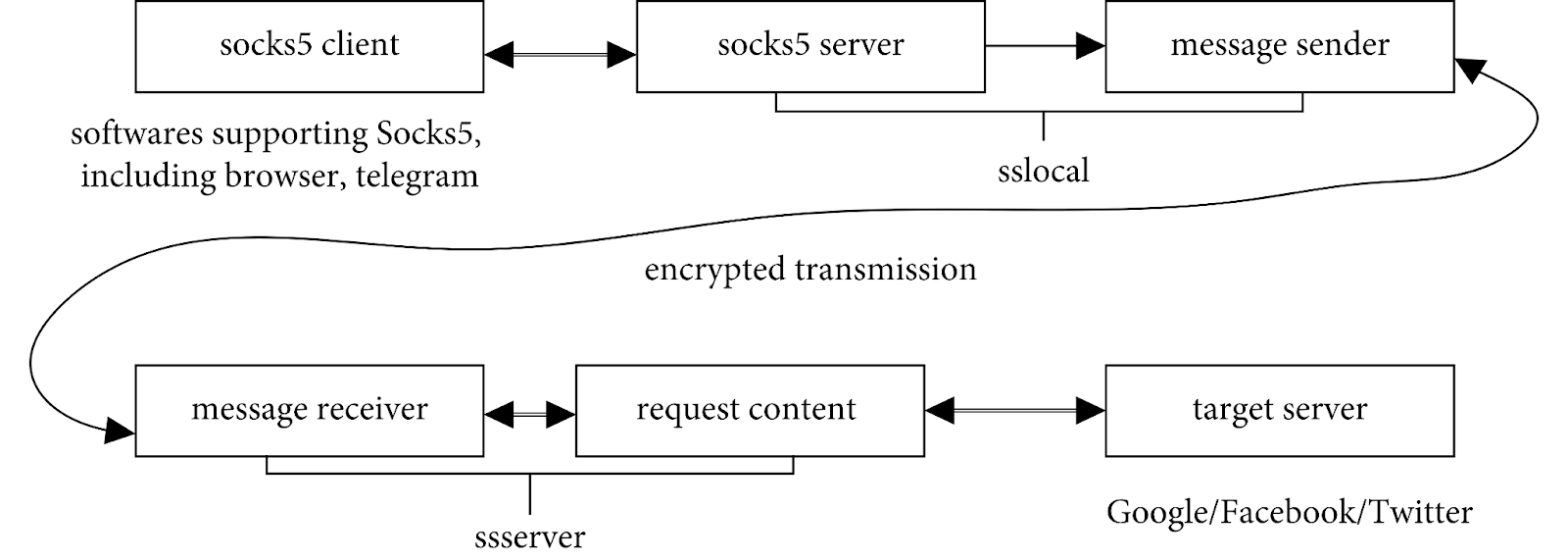
Das Prinzip von Shadowsocks: Für SS-Programme wird es wie ein gewöhnliches SOCKS5 organisiert, aber mit der IP-Adresse 127.0.0.1. Diese IP nennt man Localhost, die Verbindung wird lokal hergestellt. Das heißt, jedes Programm, zum Beispiel ein Browser, verbindet sich mit demselben Gerät, auf dem es läuft. Dann wird eine Verbindung zwischen der lokalen Shadowsocks-Komponente und dem Server aufgebaut, in der der Verkehr bereits verschlüsselt ist.
Mehr Details finden Sie in dem Video zum Umgehen der Großen Chinesischen Firewall.
Sie können andere Anwendungen mit Shadowsocks verbinden, und der Proxy funktioniert nur für ausgewählte Anwendungen. Wenn eine davon keinen Proxy unterstützt, können Sie zum Beispiel Proxifier verwenden.
Zur Installation und Konfiguration von Shadowsocks benötigen Sie ein gewisses Verständnis für Verbindungen. Folgendes brauchen Sie zum Start:
- Kaufen und konfigurieren Sie einen VPS-Server in einem Land, in dem die gewünschten Inhalte nicht blockiert sind, oder verwenden Sie einen fertigen Proxy-Server, der auf Websites mit Shadowsocks-Proxys zu finden ist.
- Client-Server. Es gibt eine mobile Anwendung im Google Play Store, das Programm für den PC kann für Windows und für Linux heruntergeladen werden.
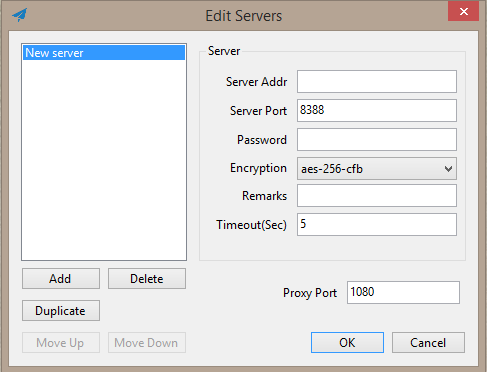
Installieren und starten Sie einfach den Client und konfigurieren dann die Verbindung zum Server: Fügen Sie die IP-Adresse, den Port, das Passwort und die Verschlüsselungsmethode des Servers hinzu.
Shadowsocks bietet drei Verbindungsmodi an:
- Direktverbindungsmodus leitet Ihren Verkehr nicht über einen Proxyserver weiter. Vorgefertigte Einstellungen für einige Anwendungen funktionieren in diesem Modus.
- PAC-Modus: Der Datenverkehr wird über einen Proxyserver geleitet, wenn Sie auf blockierte Websites zugreifen.
- Im globalen Modus wird der gesamte Datenverkehr über einen Proxyserver umgeleitet.
Shadowsocks kann eine HTTPS-Verbindung zu einem entfernten Server simulieren, um den Verkehr zu verschleiern. So versteht der Anbieter nicht, was der Nutzer gerade ansieht und welche Blockaden umgangen werden. Dieser Trick ist möglich, wenn das simple-obfs-Plugin zur Obfuskation auf dem Server installiert ist.
Obfuskation ist das Maskieren und Verwirren des Datenverkehrs. Damit können Sie sich vor Erkennung schützen: Der Anbieter kann nicht herausfinden, dass Sie Shadowsocks verwenden. Dies wird meist durch Codeverschlüsselung, Umbenennen von Variablen in sinnlose Namen, Hinzufügen unnötigen Codes oder Verwendung von Lösungen wie Cloak, Stunnel, OpenVPN Scramble usw. erreicht.
Die chinesischen Behörden verfolgen den Betrieb von Shadowsocks mittels passiver Verkehrsanalyse und aktivem „Probing“ und blockieren die Verbindungen trotz Obfuskation. Zuerst sucht die Firewall nach möglichen Shadowsocks-Verbindungen; im zweiten Schritt verbindet sie sich von eigenen IP-Adressen aus als Shadowsocks-Client mit den Servern und beobachtet deren Antworten.
Details und Lösungsmechanismen sind auf GitHub beschrieben, aber in jedem Fall funktioniert Shadowsocks besser als VPN.
Vorteile
1) Selektive Traffic-Maskierung. Sie können angeben, welcher Verkehr über den Anbieter und welcher über Shadowsocks geleitet wird. So können Sie Blockaden umgehen und gleichzeitig Zugang zu bestimmten Diensten behalten.
Beispiel: gleichzeitige Nutzung von Instagram und staatlichen Online-Diensten. Ersterer ist in Ihrem Land eventuell gesperrt, letztere funktionieren nur mit lokalen IP-Adressen. VPN ermöglicht Zugriff auf Instagram, blockiert aber lokale Dienste. Einige VPNs unterstützen Split-Tunneling. Mit Shadowsocks lösen Sie dieses Problem: Sie maskieren Instagram-Verkehr und nutzen parallel andere Dienste.
2) Schutz vor DPI. DPI (Deep Packet Inspection) ist eine Technologie zur Überwachung des Datenverkehrs bestimmter Anwendungen. Shadowsocks ist schwer zu erkennen und zu blockieren, da es eine reguläre HTTPS-Verbindung imitiert. Dennoch ist Shadowsocks anfällig für aktives Probing und Mustererkennung. Im Gegensatz zu fortgeschritteneren Transportern (z. B. Obfs4) kann es von ausgefeilten Firewalls erkannt und blockiert werden.
3) Zuverlässigkeit. Shadowsocks fällt bei Verbindungsabbrüchen nicht aus, wenn es als alleiniger Kanal konfiguriert ist. Bei Verlust der VPN-Verbindung läuft der Datenverkehr direkt, und der Anbieter sieht alle Informationen. KillSwitch löst dieses Problem teilweise, indem es die Internetverbindung sofort trennt, wenn die VPN-Verbindung verloren geht. Allerdings funktioniert es manchmal nicht oder ist nicht vorhanden.
4) Gute Bandbreite. Richtig konfiguriert arbeitet Shadowsocks schneller als andere Verschlüsselungsmethoden wie SSH-Tunneling oder VPN. Geschwindigkeitsverlust liegt bei etwa 3–5 %.
5) Universalität. Es gibt Clientprogramme für alle Betriebssysteme – Windows, MacOS, Linux (verschiedene Distributionen), Android und iOS.
6) Geringere Rechenlast bei der Verschlüsselung. Aus Sicht des Clients spart das Akku (wichtig für mobile Geräte), und aus Sicht des Servers Ressourcen auf dem VPS/VDS.
7) Kostenersparnis. Für Shadowsocks reicht der billigste VPS-Server. Idealerweise bietet der Hosting-Anbieter unbegrenzten Traffic mit VPS/VDS. Das ist deutlich günstiger als ein kostenpflichtiger VPN-Service. Man kann auch fremde Proxys verwenden, aber Angebote wie WannaFlix oder 12VPN sind deutlich teurer als ein eigener Server – etwa 10 US-Dollar im Monat.
Zum Vergleich: Ein VPS mit 5 GB Speicher, 0,5 GB RAM und unbegrenztem Traffic kostet ca. 0,87 US-Dollar monatlich, was für Shadowsocks ausreicht. Die günstigsten VPN-Dienste kosten meist ab 2 US-Dollar im Monat und verlangen oft eine Vorauszahlung für 2–3 Jahre. Kostenlose VPNs werden nicht berücksichtigt, da sie Daten begrenzen und Geschwindigkeit sowie Traffic drosseln.
Nachteile
1) Komplexität der Nutzung. Man muss verstehen, wie PCs und Verbindungen funktionieren, obwohl die Konfiguration nur 5 Zeilen umfasst. VPNs sind deutlich einfacher.
2) Risiko von Geschwindigkeitsverlust. Je nach verwendeten Obfuskatoren kann die Internetgeschwindigkeit stark sinken.
3) Begrenzte Nutzbarkeit. Man kann versuchen, die Region bei Netflix zu ändern, aber diese Methode hält nicht lange, da der Dienst Umgehungssysteme überwacht. Für Torrents ist es keine gute Lösung: Wenn Sie einen Server mieten, können Ihre persönlichen Daten leicht ermittelt und Urheberrechtsverletzungen vorgeworfen werden.
4) Begrenzte Verfügbarkeit. Trotz Popularität ist es in einigen Regionen schwierig, zuverlässige VPS-Server zu kaufen oder sich mit ihnen zu verbinden.
5) Kein offizielles Audit. Viele Experten haben den Open-Source-Code von Shadowsocks geprüft, aber es gab kein offizielles Audit wie etwa bei OpenVPN durch OSTIF. Ein offizielles Audit würde die Sicherheit erhöhen. Der Code ist relativ einfach, was das Risiko von gefälschten Softwarepaketen erhöht.
Shadowsocks vs WireGuard
Was ist WireGuard?
WireGuard ist ein modernes VPN-Tool, das Ihre Internetverbindung absichert. Stellen Sie sich einen privaten Tunnel zwischen Ihrem Gerät (Laptop, Handy) und dem Internet vor. Alles, was Sie senden oder empfangen, läuft durch diesen Tunnel, sodass Hacker oder Lauscher in öffentlichen WLANs nichts sehen können. WireGuard ist:
- Schnell: Minimale Verzögerung im Vergleich zu traditionellen VPNs.
- Einfach: Installation, Hinzufügen eines „Servers“ oder „Peers“ und ein Schalter zum Verbinden.
- Sicher: Nutzt aktuelle Verschlüsselung, um Ihre Daten zu schützen.
Sie können WireGuard nutzen, wenn Sie in öffentlichen WLANs sind, so tun möchten, als würden Sie aus einem anderen Land surfen, oder einfach Ihre Online-Aktivitäten privat halten wollen.
Kryptografie-Suite von WireGuard
- Schlüsselaustausch: Curve25519
- Verschlüsselung & Authentifizierung: ChaCha20-Poly1305 AEAD
- Hashing: BLAKE2s für Datenintegrität und HMAC
Architektur von WireGuard
- Ein einzelner UDP-Port pro Schnittstelle, minimiert Angriffsfläche und erleichtert Firewall-Durchquerung.
- Stateless-Handshake mit ephemeren Schlüsseln: Peers erzeugen alle 120 Sekunden neue Sitzungsschlüssel, ohne Verbindungsstatus zu speichern.
Unterschied zwischen Shadowsocks und WireGuard
Shadowsocks ist ideal, wenn Sie eine schnelle, app-spezifische Lösung zum Umgehen von Zensur (z. B. zum Entsperren einer Website oder eines Streaming-Dienstes) benötigen, ohne die VPN-Einstellungen Ihres Systems zu ändern. WireGuard eignet sich besser für vollständigen Geräteschutz, sichere Site-to-Site-Tunnel oder wenn Sie ein robustes, geprüftes VPN mit minimaler Latenz und starken kryptografischen Garantien für das gesamte Netzwerk benötigen.
Merkmal | Shadowsocks | WireGuard |
|---|
Typ | Verschlüsselter SOCKS5-ähnlicher Proxy | Layer-3 VPN-Tunnel |
Hauptanwendungsfall | Zensurumgehung & App-spezifisches Proxying | Site-to-Site oder Gerätweites VPN |
Protokollschicht | Anwendungsschicht | Netzwerkschicht (IP) |
Verschlüsselung | AEAD-Chiffren (z. B. ChaCha20-Poly1305, AES-GCM) | Noise Protocol Framework (ChaCha20-Poly1305, Curve25519, BLAKE2s) |
Authentifizierung | Geteilter geheimer Schlüssel; kein integrierter Schlüsselaustausch | Public-Key-Kryptographie mit integriertem Schlüsselaustausch |
Performance | Leichtgewichtig, user-space; geringe Overhead | Extrem schnell, Kernel- oder optimierte Implementierung |
Erkennungsschutz | Kann durch DPI erkannt werden, wenn nicht obfuskiert | Statischer UDP-Port/-Protokoll; schwerer zu erkennen als generisches VPN |
Setup & Deployment | Einfach: Client installieren, Proxyserver angeben | Benötigt Kernel-Modul oder unterstützten Client, Root-Rechte und Routing-Konfiguration |
Routing-Umfang | Pro Anwendung (Browser, bestimmte App) | Gesamtes Netzwerk (aller Datenverkehr) |
Shadowsocks vs OpenVPN
Was ist OpenVPN?
OpenVPN ist eine beliebte und vertrauenswürdige VPN-Technologie, die eine sichere, verschlüsselte Verbindung („Tunnel“) zwischen Ihrem Gerät und einem anderen Netzwerk über das Internet herstellt. Dieser Tunnel schützt Ihre Daten vor Abhören, ermöglicht privates Surfen und kann so erscheinen lassen, als würden Sie aus einem anderen Standort zugreifen. OpenVPN ist ein Open-Source-VPN-Protokoll und eine Software, die sichere Punkt-zu-Punkt- oder Site-to-Site-Verbindungen mit SSL/TLS für den Schlüsselaustausch implementiert.
OpenVPN wird verwendet, um:
- Privatsphäre in öffentlichen WLANs zu schützen
- Regionale Inhalte freizugeben
- Sicher remote auf Arbeitsplatznetzwerke zuzugreifen
OpenVPN-Verschlüsselung: Unterstützt robuste kryptografische Algorithmen wie AES (Advanced Encryption Standard) zur Datenvertraulichkeit.
OpenVPN-Authentifizierung: Nutzt X.509-Zertifikate für gegenseitige Authentifizierung, mit optionalem Benutzername/Passwort und Pre-Shared Keys.
OpenVPN-Transportprotokolle: Arbeitet über UDP oder TCP, was Flexibilität für verschiedene Netzwerkumgebungen und Firewall-Durchquerung bietet.
OpenVPN-Tunneling: Arbeitet auf Netzwerkebene (Layer 3), erstellt virtuelle Netzwerkschnittstellen (TUN) oder bridged Ethernet-Frames (TAP).
Unterschied zwischen Shadowsocks und OpenVPN
Shadowsocks eignet sich hervorragend für leichte, app-spezifische Umgehung von Zensur mit minimaler Latenz, besonders in restriktiven Umgebungen. OpenVPN ist eine robuste, gut geprüfte VPN-Lösung für das gesamte Gerät oder Netzwerk, bietet stärkere Sicherheit und breitere Anwendungsfälle, erfordert jedoch eine komplexere Einrichtung und höheren Ressourcenverbrauch.
Merkmal | Shadowsocks | OpenVPN |
|---|
Typ | Verschlüsselter SOCKS5-Proxy | Vollständiges VPN-Protokoll |
Hauptnutzung | Zensurumgehung, leichter Proxy | Sicherer Fernzugriff, Site-to-Site VPN |
Protokollebene | Anwendungsebene | Netzwerkebene (Layer 3) VPN-Tunnel |
Verschlüsselung | AEAD (ChaCha20-Poly1305, AES-GCM) | SSL/TLS mit konfigurierbaren Chiffren (AES, ChaCha) |
Authentifizierung | Pre-Shared Key | Zertifikate, Benutzername/Passwort oder Pre-Shared Keys |
Traffic-Obfuskation | Standardmäßig begrenzt; Plugins für Obfuskation möglich | SSL-Obfuskation und Plugins wie Obfsproxy möglich |
Erkennungsschutz | Mittel; anfällig für Deep Packet Inspection ohne Obfuskation | Stärker ab Werk; schwerer zu blockieren oder zu erkennen |
Leistung | Leichtgewichtig, niedrige Latenz | Höherer Overhead, aber stabil und sicher |
Einrichtung | Einfache Konfiguration für Proxy-Clients | Komplexer; erfordert Zertifikatsverwaltung und Routing-Konfiguration |
Routing-Umfang | Pro Anwendung (Browser, spezifische App) | Gesamtes Gerät oder Netzwerkverkehr |
Anwendungsfälle | Schneller Zensurumgehung, einzelne App-Proxy | Enterprise VPN, sicherer Fernzugriff, Privatsphäre |
Shadowsocks vs ShadowsocksR
Was ist ShadowsocksR (SSR)
Aktuell hat Shadowsocks eine Community und eine eigene Website. Enthusiasten können darauf basierende Lösungen erstellen. Nach der Schließung von Shadowsocks 2015 behauptete der Entwickler breakwa11, dass SS leicht erkennbar sei. Er erstellte ShadowsocksR, eine auf Shadowsocks basierende Version mit Unterstützung für Traffic-Obfuskation. Somit ist ShadowsocksR ein Fork des Originalprotokolls, geschrieben in Python, mit Traffic-Obfuskation und Erkennungsvermeidung.
Empfohlen wird meist die aktuelle Version Shadowsocks-Rust auf Rust-Basis.
Wichtige Punkte zu ShadowsocksR:
- Erweiterte Obfuskation: SSR fügt fortgeschrittene Methoden hinzu, um Proxy-Traffic zu verschleiern und Erkennung durch DPI-Systeme, wie die chinesische Große Firewall, zu erschweren.
- Mehrere Protokoll- und Obfuskationsoptionen: Im Gegensatz zu Shadowsocks, das einen relativ einfachen SOCKS5-Proxy mit Verschlüsselung nutzt, unterstützt SSR verschiedene Plugins, die Paketheader ändern, Verkehrsmuster randomisieren und Filter umgehen.
- Abwärtskompatibilität: SSR ist größtenteils kompatibel mit Shadowsocks-Clients, benötigt aber eigene oder kompatible Clients für volle Funktionalität.
- Keine offizielle Wartung: SSR ist ein Community-Projekt mit mehreren unabhängigen Versionen und nicht Teil des offiziellen Shadowsocks-Repositories.
- Kontrovers: Einige Datenschutzexperten bezweifeln die Sicherheit und Wartung von SSR und empfehlen offizielle Shadowsocks oder modernere Tools wie V2Ray für sichere, geprüfte Proxy-Lösungen.
Zusammenfassend wurde ShadowsocksR entwickelt, um Shadowsocks-Verkehr schwerer erkennbar und blockierbar zu machen, wird heute aber weniger verwendet und offiziell nicht unterstützt.
Shadowsocks vs SOCKS5
Shadowsocks arbeitet auf dem SOCKS5-Protokoll. Einfach gesagt, es ist wie Ihre Lieblings-App auf iOS. Shadowsocks fügt SOCKS5 mehr Sicherheit hinzu.
Hier ist der Unterschied zwischen Shadowsocks und SOCKS5:
Aspekt | SOCKS5 Proxy | Shadowsocks |
|---|
Definition | Ein allgemeines Proxy-Protokoll, das Netzwerkpakete auf TCP-Ebene zwischen Client und Server weiterleitet. | Ein verschlüsseltes Proxy-Protokoll basierend auf SOCKS5 mit starker Verschlüsselung und Obfuskation. |
Verschlüsselung | Standardmäßig keine; plain TCP-Weiterleitung | Verwendet AEAD-Verschlüsselung (z. B. ChaCha20-Poly1305) zum Schutz der Datenübertragung. |
Zweck | Einfacher Proxy zum Umgehen von IP-Blocks oder zur Weiterleitung von Verkehr | Entwickelt für Zensurumgehung mit Fokus auf Privatsphäre und Sicherheit. |
Erkennungsrisiko | Hoch — Verkehr ist unverschlüsselt und leicht erkennbar | Niedrig — verschlüsselt den Verkehr und kann mit Obfuskations-Plugins DPI umgehen. |
Einrichtungsaufwand | Einfach; von vielen Clients unterstützt | Benötigt spezielle Shadowsocks-Clients oder kompatible Software. |
Anwendungsfall | Basis-Proxynutzung, Zugriff auf gesperrte IPs | Sicheres Umgehen von Internetsperren und Schutz der Datenprivatsphäre. |
Shadowsocks vs UDP over TCP
Was ist UDP over TCP?
UDP over TCP bezeichnet das Tunneln von UDP-Verkehr (verbindungslos, z. B. für Gaming, VoIP, DNS) innerhalb von TCP-Verbindungen (verbindungsorientiert und zuverlässig). Dies wird manchmal von VPNs oder Proxys verwendet, die nur TCP unterstützen, um UDP-Pakete zu transportieren. Das verursacht zusätzliche Latenz, Jitter und Performanceverluste, weil TCP-Retransmissionen nicht gut zum Low-Latency-Design von UDP passen. Es hilft aber manchmal, wenn UDP blockiert wird oder nur TCP erlaubt ist.
Wesentliche Unterschiede zwischen UDP over TCP und Shadowsocks
Merkmal | UDP over TCP | Shadowsocks |
|---|
Verkehrsart | UDP-Pakete in TCP-Streams gekapselt | Native Unterstützung für TCP- und UDP-Verkehr |
Leistung | Kann durch TCP-Retransmissionen Verzögerungen und Jitter verursachen | Optimiert für minimale Latenz mit nativer UDP-Unterstützung |
Anwendungsfall | Verwendung, wenn UDP blockiert oder nicht unterstützt wird | Entwickelt für Zensurumgehung und sicheres Proxyn |
Erkennungsschutz | Abhängig vom zugrundeliegenden TCP-Tunnel; meist erkennbar | Verschlüsselt und obfuskiert, schwerer zu erkennen |
Protokollkomplexität | Einfaches Tunneling | Komplettes verschlüsseltes Proxy-Protokoll mit Handshake und Verschlüsselung |
VPN vs Shadowsocks
VPN und Shadowsocks sind verschiedene Werkzeuge. Das eine ist ein virtuelles privates Netzwerk, über das wir im Blog geschrieben haben, das andere ein Proxy-Protokoll. Technisch gesehen:
- Verschlüsseln sie den Verkehr
- Helfen sie, Blockaden zu umgehen
Shadowsocks verwendet jedoch einfachere Verschlüsselung und ermöglicht keine Anonymität im Internet. Das Projekt wurde ursprünglich weniger für Sicherheit als zur Umgehung der chinesischen Firewall entwickelt. Dieses Problem wurde teilweise in ShadowsocksR adressiert, auf das wir am Ende eingehen. VPNs nutzen meist den komplexen AES-256-Algorithmus.
VPN-Dienste bieten oft viele Zusatzfunktionen, z. B. KillSwitch. VPN ist ein „Tunnel“, wenn dieser nicht mehr funktioniert, läuft der Datenverkehr direkt und die echte IP kann preisgegeben werden. KillSwitch schützt davor, indem er die Internetverbindung sofort trennt, wenn der VPN-Zugang verloren geht.
Außerdem verfügen VPNs über ein riesiges Servernetzwerk. Man kann aus verschiedenen Ländern auf das Internet zugreifen – die IP-Adresse ändert sich jeweils zum Land des gewählten Servers.
Fazit: VPN ist bequemer, sicherer und einfacher. Wenn es verfügbar ist und Ihren Anforderungen entspricht, nutzen Sie es. Gibt es Schwierigkeiten, löst Shadowsocks das Problem: Es funktioniert besser in Ländern, wo VPNs blockiert sind und starke Einschränkungen bestehen. Der Datenverkehr ähnelt HTTPS und erregt keine Verdachtsmomente. Mehrere TCP-Verbindungen ermöglichen hohe Geschwindigkeit. Es ist kosteneffektiver für einfache Umgehung von Blockaden.
Wichtige Unterschiede zwischen Shadowsocks und VPN
| Shadowsocks | VPN |
|---|
Verschlüsselung | Schwächere Verschlüsselung im Vergleich zu den meisten VPNs | Zuverlässigere Verschlüsselung nur zwischen Gerät und Server |
Zugriff auf Inhalte | Umgeht Internetzensur und ermöglicht Zugang zu blockierten Inhalten | Umgeht ebenfalls Zensur, ist aber leichter erkennbar |
Leistung | Schneller durch weniger Verschlüsselung und kürzeren Pfad | Langsamer wegen Verschlüsselung und zusätzlichem Weg zum VPN-Server |
Konfigurationskomplexität | Für normale Nutzer schwieriger einzurichten und zu nutzen | Relativ einfach zu konfigurieren und zu nutzen |
Kosten | Günstige oder sogar kostenlose Optionen | Teurer, besonders für hochwertige Dienste |
Anwendungsfälle | Für die Umgehung komplexer Firewalls (z. B. China) und Zugang zu Blockaden | Für Nutzer, die Wert auf Privatsphäre und Zugang zu Inhalten legen |
Shadowsocks vs Mobile Proxies
Was sind Mobile Proxies?
Mobile Proxies sind echte IPs mobiler Netze, die von Mobilfunkanbietern über dedizierte Geräte mit SIM-Karten bereitgestellt werden. Sie bieten hoch vertrauenswürdige, dynamische und standortbezogene IP-Adressen, die viel schwerer zu erkennen oder zu blockieren sind.
Vergleichstabelle zwischen Mobile Proxies und Shadowsocks
Aspekt | Shadowsocks | Mobile Proxies |
|---|
Was es ist | Ein verschlüsseltes Proxy-Protokoll (basierend auf SOCKS5) zum Umgehen von Zensur mit Verschlüsselung und Weiterleitung des Datenverkehrs über einen Remote-Server | Echte Proxys auf mobilen Geräten oder SIM-Karten, die Mobilfunknetze (LTE/4G/5G) zur Verkehrsweiterleitung nutzen |
Technologie | Softwarebasierter Proxy mit Verschlüsselung, läuft auf VPS oder Server | Hardwarebasierter Proxy, der an Mobilfunkanbieter gebunden ist, mit echten mobilen IP-Adressen |
IP-Adressentyp | Meist Datenzentrum-IP-Adressen, die leicht blockiert oder markiert werden können | Echte IPs von Mobilfunkanbietern, sehr vertrauenswürdig und dynamisch, an geografische Standorte gebunden |
Erkennungsrisiko | Mittel — kann durch DPI erkannt werden, sofern keine Obfuskation verwendet wird | Niedrig — Verkehr sieht aus wie legitime Nutzung eines Mobilfunknetzes, schwerer zu blockieren oder zu markieren |
Leistung | Abhängig vom Serverstandort und Netzwerk; generell schnell, variiert aber | In der Regel schnell mit stabilem LTE/4G/5G; IPs rotieren natürlich |
Anwendungsfälle | Zensurumgehung, Schutz der Privatsphäre, Entsperren von Websites und Diensten | SEO, SMM, Werbeüberprüfung, Kontoerstellung, Mobile App Testing und alle Aufgaben, die vertrauenswürdige mobile IPs erfordern |
Einrichtung | Erfordert Installation von Client-Software und Proxy-Konfiguration | Meist über Marktplatz oder API zugänglich; keine Client-Software nötig, nur Proxy-Zugangsdaten |
Anonymitätsniveau | Gute Verschlüsselung, aber IP kann aus Rechenzentren stammen | Sehr hohes Vertrauen und Anonymität, da IPs zu Mobilfunkanbietern gehören und dynamisch rotieren |
Was sollte ich verwenden – Shadowsocks oder Mobile Proxies?
Für Zensurumgehung und verschlüsseltes Proxying – Shadowsocks.
Für authentische mobile IPs, vertrauenswürdigen standortbezogenen Zugang und geringes Erkennungsrisiko sind Mobile Proxies überlegen – besonders für Business- und Automatisierungsanwendungen.
Fazit
Shadowsocks ist ein kostengünstiges und praktisches Tool zum Umgehen von Blockaden. Es kann auch für den Schutz von Verbindungen nützlich sein. Natürlich hat es weniger Funktionen als ein VPN, ist aber etwas schneller. Für einfache Aufgaben wie die Wiederherstellung des Zugangs zu blockierten Seiten ist es optimal. Es ist einfach zu bedienen und zu konfigurieren; es gibt viele Anleitungen im Internet.
English
Español
Français
Bahasa Indonesia
Polski
Português
Русский
Українська
简体中文